2365: Messaging Systems
Explanation
| |
This explanation may be incomplete or incorrect: Created by AN UNENCRYPTED SMS. Please mention here why this explanation isn't complete. Do NOT delete this tag too soon. If you can address this issue, please edit the page! Thanks. |
Messaging systems suffers from the Network effect, as in order to communicate, both parties need to have adopted the same system. Though relatively ancient by modern standards, SMS is supported by most every mobile device that has a phone number attached, which means if you want to send a message to someone, but aren't sure if they have insert messaging app here, you can be sure at least they have SMS.
SMS is a text messaging service formally defined in the GSM standard in 1985 and first used in 1992. It limits users to being able to send up to 160 characters.
The comic mentions many other communication systems, which offer various advantages in either security and or a bunch of general improvements filed under the label "vaguely modern", such as longer character limits and the ability to share media such as images in-service.
Vaguely Modern
Slack
Slack is a workplace messaging service which offers the ability for administrators to create channels in order to organize the discussion. It is asynchronous, which means that conversations can occur out of time, hours apart from each other. It also keeps track of every message, and everything in a public channel stays there forever for everyone to see. It is not encrypted, and has been moving towards being less privacy focused for end users over the years as corporate demand for employee surveillance has prompted the company to offer ever more invasive services to administrators. Overall, it is a popular service with some large companies and non-profit organisations, but does not yet have universal adoption.
Facebook Messenger
Hangouts
Discord
Various DMs
Vaguely Modern & E2E Encrypted
Signal
iMessage
E2E Encrypted
PGP Email
Various Obscure Projects
Skype I Think
Jabber + TLS
Supported By Everyone
SMS
Transcript
| |
This transcript is incomplete. Please help editing it! Thanks. |
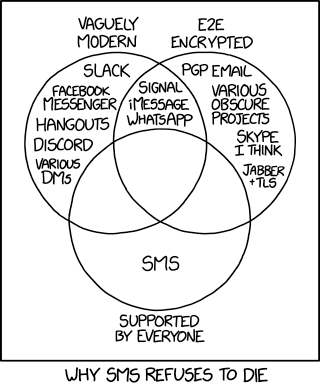
A Venn Diagram is shown, framed in a box. It has three components:
Vaguely Modern, E2E Encrypted, Supported By Everyone
Solely in the Vaguely Modern category are:
Facebook Messenger, Hangouts, Discord, Various DMs
In both 'Vaguely Modern' and 'E2E Encrypted' categories are:
Signal, iMessage, Whatsapp
Solely in the E2E Encrypted category are:
PGP Email, Various Obscure Projects, Skype I think, Jabber + TLS
Solely in the 'Supported By Everyone' category is:
SMS
All other categories are empty.
- [Caption Below the Comic]: Why SMS refuses to die
Discussion
I guess ordinary email should be in the same section as SMS as well. 162.158.158.171 00:20, 29 September 2020 (UTC)
The comic should mention MMS, which is well integrated into SMS, so that it's supported by not quite as much as SMS but still by almost everybody, and counts as vaguely modern in that you can attach images and have no length limit. ―TobyBartels (talk) 00:46, 29 September 2020 (UTC)
My DynaTAC doesn't get SMS. --172.69.22.150 00:56, 29 September 2020 (UTC)
Okay, got a basic explanation up; The comic is missing a bunch of different messaging services I feel. Also, I knew that somebody would say that their phone doesn't support SMS, I guess that habit of hedging writing with mostly is paying off. 172.69.63.143 01:01, 29 September 2020 (UTC)
"It [Whatsapp] is popular in multiple countries, namely Latin America and India." I have no idea what this means: should "namely" be "mainly"? But is the fixed version even true? 162.158.158.225 11:28, 29 September 2020 (UTC)
- Both "namely" and "mainly" are valid and mean very similar things in this context. Saying "... mainly Latin America and India" suggests most of Whatsapp's popularity is in Latin America and India and Whatsapp has little popularity anywhere else. On the other hand, saying "... namely Latin America and India" suggests that Latin America and India are some of the countries where Whatsapp is particularly popular without implying that Whatsapp is significantly unpopular elsewhere. That said, it's a pretty subtle distinction that almost no one will actually care about except hardcore language geeks. With love from your friendly neighborhood Grammar Communist. <3 Gertuviti (talk) 12:57, 29 September 2020 (UTC)
- In any case: Wouldn't it be easier to list countries where it's not popular? Because to what I know there are a few markets where it didn't get a foothold (namely Northern America, Australia, China), but in most of the rest of the world it basically is the way of messaging since many years (others, like Signal, Telegram, Threema, are coming, but usually have a hard time fighting WhatsApp predominancy). SMS didn't disappear and is still used by some technical systems (like for sending TANs or alarms), but I can't remember when I last heard about someone sending an SMS privately (my current phone, in service since one year, for sure never received one). --YMS (talk) 14:17, 29 September 2020 (UTC)
- FIFY by avoiding both terms, & by adding the missing "in." Your friendly & useful Grammar democratic republican.
- This Grammar socialist-conservative thinks "in multiple countries, especially India & in Latin America" has other issues. I appreciate the need for "countries, especially (...) in Latin America" to be integrated with "countries, especially India (...)", but the mix of the multiple and singular examples as equivalent list-subitems jars. The "Set of (Item, Set of (Items))" thing is a complex linguistic construct. Perhaps "in multiple regions, especially India and Latin America" works better (both qualify as regions, or contain more implicitly relevent sub-regions if you prefer that interpretation, without worrying about precise country-level boundries). This also switches the ampersand out (incongruous eyesore, an unnecessary abbr. that clashes with the "in; and, particularly if used as the reordered "in Latin America & India", would actually imply stronger linking than merely being two examples plucked from a clearly unexhausted larger list). But I leave this suggestion here only for consideration. 141.101.98.52 16:04, 30 September 2020 (UTC)
- I now removed the list completely. While India has the highest absolute number of WhatsApp users for sure (400 million - only China would theoretically be able to top that, but WhatsApp basically is not used there), and Brazil probably comes second with some 120 million users, WhatsApp has a higher market share in many other countries, with more than 80% of smartphone owners using WhatsApp in a whole bunch of European countries, for example. All in all it totals to over 2 billion users per https://blog.whatsapp.com/two-billion-users-connecting-the-world-privately - I don't think we should highlight just two regions when a quarter of the world population is said to use WhatsApp. --YMS (talk) 23:21, 2 October 2020 (UTC)
- This Grammar socialist-conservative thinks "in multiple countries, especially India & in Latin America" has other issues. I appreciate the need for "countries, especially (...) in Latin America" to be integrated with "countries, especially India (...)", but the mix of the multiple and singular examples as equivalent list-subitems jars. The "Set of (Item, Set of (Items))" thing is a complex linguistic construct. Perhaps "in multiple regions, especially India and Latin America" works better (both qualify as regions, or contain more implicitly relevent sub-regions if you prefer that interpretation, without worrying about precise country-level boundries). This also switches the ampersand out (incongruous eyesore, an unnecessary abbr. that clashes with the "in; and, particularly if used as the reordered "in Latin America & India", would actually imply stronger linking than merely being two examples plucked from a clearly unexhausted larger list). But I leave this suggestion here only for consideration. 141.101.98.52 16:04, 30 September 2020 (UTC)
- FIFY by avoiding both terms, & by adding the missing "in." Your friendly & useful Grammar democratic republican.
- In any case: Wouldn't it be easier to list countries where it's not popular? Because to what I know there are a few markets where it didn't get a foothold (namely Northern America, Australia, China), but in most of the rest of the world it basically is the way of messaging since many years (others, like Signal, Telegram, Threema, are coming, but usually have a hard time fighting WhatsApp predominancy). SMS didn't disappear and is still used by some technical systems (like for sending TANs or alarms), but I can't remember when I last heard about someone sending an SMS privately (my current phone, in service since one year, for sure never received one). --YMS (talk) 14:17, 29 September 2020 (UTC)
Discord is slowly moving towards supported by everyone because of Covid-19. Stardragon (talk) 12:27, 29 September 2020 (UTC)
"Discord being used by everyone" (ref. Explanation rather than above Talk comment), I have deliberately kept off Discord, so clearly not. The reason for Discord (as per Talk comment) applies more so to Zoom/Teams, though. Although I've kept off those too, where I can (using Zoom on a Raspberry Pi on a few occasions, which tends to overheat it). 162.158.159.140 13:45, 29 September 2020 (UTC)
- Good for you; you're fighting the system! Note that the explanation has been updated from "everyone" to "many groups". OhFFS (talk) 18:02, 29 September 2020 (UTC)
Separate comment: I'm not sure if this helps or hinders the comic's assertions, but friends and family continually tend to send Texts to my dumb-phone that contain emoji I keep telling them that it can't show (i.e. any of them). Only by context can I guess if the anonymous 'square' character is more thumbs-up/smiley-face or otherwise. Or if the three squares after the birthday greeting might include candles/cake. Making them no more clarified than the plain-text message they think they're clarifying. I suppose the single, sole 'emojibox' reply does work as a basic read-receipt notification, though. Regardless of if it's actually winky-face, poo, zombie, rainbow, cablecar, flag-of-Liberia or whatever they decided to send me... ;) 162.158.159.140 13:45, 29 September 2020 (UTC)
- That's one reason why SMS isn't in the "Vaguely Modern" category. Although it can transmit and receive emojis, many devices that only support SMS can't display them. Barmar (talk) 14:28, 29 September 2020 (UTC)
Why isn't there a category for Venn Diagrams? Barmar (talk) 18:58, 29 September 2020 (UTC)
- Uh, yes there is... — The 𝗦𝗾𝗿𝘁-𝟭 talk stalk 11:31, 30 September 2020 (UTC)
Aww, Telegram didn't even get mentioned, despite having 200 times as many users as Signal. :( Fabian42 (talk) 21:26, 29 September 2020 (UTC)
- Telegram is not really E2E encrypted by default. One-on-one conversations can be upgraded to E2E encryption ("secret chat") but group conversations not at all. -> From the horse's mouth. 141.101.98.164 20:24, 2 October 2020 (UTC)
I for one would support using Randall's local-mobile-TID-gateway protocol 173.245.52.157 22:41, 29 September 2020 (UTC)
- Whatsapp is also used as main service in most of the European Union, to the point even everybody with iPhones or access to iMessage is using it as main protocol, and most youngsters have a habit of using it for everything instead of Email (then wondering why pictures and videos got degraded). Maybe this should be mentioned.
The Forward article at the kosher-phone link has a biased and faintly derogatory tone. The Wikipedia entry [1], while not perfect, would be a better choice. Wolfsbane2019 (talk) 20:33, 30 September 2020 (UTC)
Regarding Skype encryption:
My understanding is that Skype uses end-to-end encryption on messages from one Skype user to another, unless Microsoft has (surreptitiously) switched the user account to server-side encryption, or in cases where the other end is not a Skype contact (telephone calls, for example). The question of how to tell whether both clients are using client-side encryption seems most relevant to this explanation. (This question is not addressed by the linked source, nor any of the associated pages I found while checking it just now.) Anyone have a good phrasing to clarify this situation, in the explanation? ProphetZarquon (talk) 23:24, 30 September 2020 (UTC)
End-To-End Encryption alone only prevents casual surveillance
It should be noted in the explanation of E2E encrypted systems, that E2E encryption ≠ unsurveillable, unless the devices at each end (at a minimum) are free of third-party monitoring at the keyboard (or mic), display buffer, unprotected or protected memory, operating system, & application levels. Ensuring this would require ongoing knowledge of all operative code & hardware functions, on both devices, which is not possible on devices using closed-source hardware, firmware, or software. (For a 4G cellular phone designed to avoid closed-source dependencies, read up on the challenges met developing the PinePhone.)
Users of devices running Microsoft or Apple operating systems (among others); or Intel or AMD or Broadcom or Qualcomm chips (among others); or closed-source keyboards, system utilities, or messaging apps; can only seek out statements from those companies as assurance that their end systems are not subject to surveillance.
In most cases, such assurances cannot be made, as these providers are bound by non-disclosure requirements as part of their compliance with regulatory & intelligence agencies. Such agencies (& even third-party contractors) have repeatedly been revealed to routinely obtain access to these systems (including iOS). In rare cases where access is not already made possible by one of the two users' devices, systems, apps, or services, then trojan attempts are made.
In turn, these mandated undisclosed access methods add to unintentional vulnerabilities, providing additional attack vectors to wholly unauthorized actors, including (so far) criminal organizations, terrorist groups, openly hostile nation states, supposedly peaceful nation states (allegedly), shady copyright-enforcement providers given free rein under revised (corporate authored) legislation, & highly motivated or resource-rich individuals.
So end-to-end encryption is essentially just a barrier to casual surveillance at the network infrastructure level; it doesn't close any of the other modes of access, which we know (hopefully, from seemingly endless disclosures over the course of decades) are leveraged at will, by everybody from US intelligence agencies to hirelings in aging office buildings who-knows-where. End-to-end encryption is step 3, after step 1, which is starting with hardware known to lack backdoors or leaks, & step 2, which is running only code that has been examined for backdoors or leaks on the whole system.
Evading surveillance is primarily a matter of not getting noticed in the first place. Once one is under surveillance, it's extremely difficult to transact wireless communication with diverse peers securely.
There's no reasonable expectation of privacy from almost any of our devices, so end-to-end encryption at the app level seems like a necessary component bolted to a pile of broken parts.
Not sure how to express this without a tirade (obviously); Seems like describing E2E Encryption without context does a potentially dangerous disservice to readers seeking explanation here...
Anyone care to discuss how we can clarify the role of E2E Encryption in the most common private messaging usage scenarios?
ProphetZarquon (talk) 23:24, 30 September 2020 (UTC)
In the most common private-messaging scenarios, casual surveillance at the network infrastructure level is the only surveillance that people are actually worried about when deciding what protocol to use for communication. 1) Any security at the device level can't be a concern of the choice of messaging service - if you've got a keylogger, it's going to log your keys in all messaging services, encrypted or not. 2) If you've got highly motivated and resource-rich individuals or hostile foreign governments trying to tail you specifically, you're presumably doing something that would necessitate learning about more secure communication methods in the first place. 108.162.241.14 05:13, 2 October 2020 (UTC)
- A first-step for deliberate surveillance might even be "is traffic of this service type leaving from/arriving at this device", even with an utter sparcity of internal meta-data access due to all that being securely packaged within various E2E/E2S2E encyption envelopes and layering. Corresponding/coincident traffic at the other end of a (synchronous/live) rerouting of that data with similar cursory monitoring, regardless of how much serving/proxying happens between them, can actually link the end-users. Both originally having been 'of interest', but the known link can be enough to raise 'interest' to 'suspicion' even without necessarily knowing anything about what the link conveys.
- Eve having then correlated her Alice and Bob (and possibly Carol, David, Frank... also part of the party) this might give her enough proof to pursuade Mike to help her listen in, recruit a Wendy from the network or install a Trudy of her own into the grouping. Alternately, merely by monitoring your (encrypted) home Wifi traffic, a near-neighbour prospective burglar is said to be able to identify timeslots they might be able to exploit to sneak in.
- The general counter-measure to all this might be to freely participate in a wider 'party line' throwing huge amounts of (effectively) junk-data from everwhere and to everywhere (in the Wifi example, some people suggest putting a small and irregularly but frequently active house-pet in front of a motion-triggered camera, although you could maybe just schedule a torrent-(re)seeding of something popular for 'infill' times (from a non-wired device) or maybe cron something else of your choice that's suitably intensive/weird/useful). You could even embed your communications, steganographically, deeply and sparsely within your Social Media postings (to the world) relying on your contacts reading them (and many others, including genuinely innocent interests) at their leisure. Probably then to send any replies over other completely different channels (perhaps coordinating an organised and fall-back-laden daisy-chaining of such systems to essentially form a communications loop, with TOR-style deep-embedding to safeguard point-to-point security and resiliance).
- ...it all depends on how paranoid (reasonably or otherwise) you are, and how much you can mutually prep the whole setup (and ability to convey how to adopt future refinements) beforehand. 141.101.107.142 18:34, 4 October 2020 (UTC)