Difference between revisions of "1938: Meltdown and Spectre"
(→Explanation: title text) |
(→Explanation: Explained the shared computers concept) |
||
| Line 18: | Line 18: | ||
The {{w|Row Hammer}} problem is something entirely different. Computer memories are organized as a two-dimensional grid of rows and columns - and are physically constructed from tiny capacitors. If you apply just the RIGHT pattern of rapid changes to one row of the grid, you can cause one of the capacitors on the next row to incorrectly change state. This is a design flaw in the memory chip - and it allows (in some circumstances) programs to change data in memory locations that they have no right to change. | The {{w|Row Hammer}} problem is something entirely different. Computer memories are organized as a two-dimensional grid of rows and columns - and are physically constructed from tiny capacitors. If you apply just the RIGHT pattern of rapid changes to one row of the grid, you can cause one of the capacitors on the next row to incorrectly change state. This is a design flaw in the memory chip - and it allows (in some circumstances) programs to change data in memory locations that they have no right to change. | ||
| + | |||
| + | Ponytail mentions that we suck at building "shared computers" because Rowhammer, Spectre, and Meltdown all break down the security divisions built between programs and users. A hacker running a separate program in a separate account shouldn't be able to access your secrets, but these bugs allow them to. This is particularly dangerous for servers and the cloud, where different programs, websites, or even companies can be sharing the same hardware. | ||
The title text humorously states that as well as row hammer, computer servers also can be "hacked" by regular hammers. A zero-day vulnerability is an attack that takes advantage of a vulnerability that was discovered that day, and hasn't been patched. One might "patch" a server against this attack by plating it with stronger metal. | The title text humorously states that as well as row hammer, computer servers also can be "hacked" by regular hammers. A zero-day vulnerability is an attack that takes advantage of a vulnerability that was discovered that day, and hasn't been patched. One might "patch" a server against this attack by plating it with stronger metal. | ||
Revision as of 19:52, 5 January 2018
| Meltdown and Spectre |
 Title text: New zero-day vulnerability: In addition to rowhammer, it turns out lots of servers are vulnerable to regular hammers, too. |
Explanation
| |
This explanation may be incomplete or incorrect: Created by an unpatched computer - Please change this comment when editing this page. Do NOT delete this tag too soon. If you can address this issue, please edit the page! Thanks. |
This comic was inspired by the Meltdown (security vulnerability) and Spectre (security vulnerability) bugs in certain processors. These vulnerabilites were disclosed to the public the week of this comic. The bugs made big news because they broke the "walls" between programs, in some circumstances allowing malware to steal secrets from normal, bug-free programs.
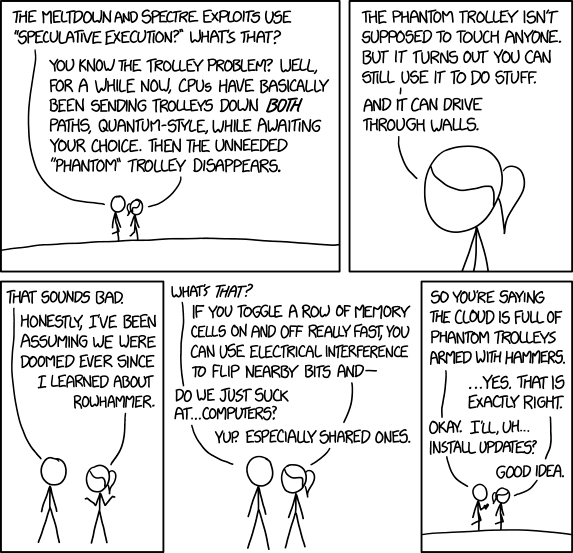
The Trolley Problem is the ethical dilemma thought experiment where an out-of-control trolley is heading to a junction (which you have control over) - to one side it'll kill one group of people - to the other, some others. Your moral dilemma is deciding which is the "best" outcome (eg, hitting a dozen five year old children or three Nobel laureats). This is like a software "if" statement. Speculative execution in most CPU chips is where the computer always takes both sides of a decision like this - explores what will happen down each path - and only causes the effects of the decision to happen when the decision as to which way to proceed is decided. This allows it to keep on doing useful work while some slower decision is made. The "quantum" aspect of this is that in some versions of quantum theory, quantum-level particles take every possible path at once and the result is the sum of all of them.
In a sense, the computer is exploring the consequences of the trolley problem in a quantum-like manner.
This would all be OK if it were not for the fact that devious black-hat hackers can come up with devious ways to see the information that should have been discarded in the "path-not-taken". So even though the computer will eventually decide that some piece of information should not be accessible - you can find out the value it would hypothetically read - even though it will soon decide that it should not access the information.
The Row Hammer problem is something entirely different. Computer memories are organized as a two-dimensional grid of rows and columns - and are physically constructed from tiny capacitors. If you apply just the RIGHT pattern of rapid changes to one row of the grid, you can cause one of the capacitors on the next row to incorrectly change state. This is a design flaw in the memory chip - and it allows (in some circumstances) programs to change data in memory locations that they have no right to change.
Ponytail mentions that we suck at building "shared computers" because Rowhammer, Spectre, and Meltdown all break down the security divisions built between programs and users. A hacker running a separate program in a separate account shouldn't be able to access your secrets, but these bugs allow them to. This is particularly dangerous for servers and the cloud, where different programs, websites, or even companies can be sharing the same hardware.
The title text humorously states that as well as row hammer, computer servers also can be "hacked" by regular hammers. A zero-day vulnerability is an attack that takes advantage of a vulnerability that was discovered that day, and hasn't been patched. One might "patch" a server against this attack by plating it with stronger metal.
Transcript
[ Cueball and Blonde are walking ]
Cueball: The Meltdown and Spectre exploits use "speculative execution." What's that?
Blonde: You know the trolley problem? Well, for a while now, CPUs have basically been sending trolleys down both paths, quantum-style, while awaiting your choice. Then the unneeded "phantom" trolley disappears.
[ Blonde framed alone, facing left. It appears they have stopped walking ]
Blonde: The phantom trolley isn't supposed to touch anyone, but it turns out you can still use it to do stuff. And it can drive through walls.
[ Cueball and Blonde are standing, facing each other ]
Cueball: That sounds bad.
Blonde: Honestly, I've been assuming we were doomed ever since I learned about Rowhammer.
[ They are still standing there. ]
Cueball: What's that?
Blonde: If you toggle a row of memory cells on and off really fast, you can use electrical interference to flip nearby bits and -
Cueball: Do we just suck at ... computers?
Blonde: Yup. Especially shared ones.
[ They resume walking to the right. ]
Cueball: So you're saying the cloud is full of phantom trolleys armed with hammers.
Blonde: ... Yes, that's exactly right.
Cueball: Okay, I'll ... install updates.
Blonde: Good idea.
Discussion
The "trolley problem" is the ethical dilemma thought experiment where an out-of-control trolley is heading to a junction (which you have control over) - to one side it'll kill one group of people - to the other, some others. Your moral dilemma is deciding which is the "best" outcome (eg, hitting a dozen five year old children or three Nobel laureats). This is like a software "if" statement. Speculative execution in most CPU chips is where the computer always takes both sides of a decision like this - explores what will happen down each path - and only causes the effects of the decision to happen when the decision as to which way to proceed is decided. This allows it to keep on doing useful work while some slower decision is made. The "quantum" aspect of this is that in some versions of quantum theory, quantum-level particles take every possible path at once and the result is the sum of all of them.
In a sense, the computer is exploring the consequences of the trolley problem in a quantum-like manner.
- There's so much wrong with this sentence. You totally did it intentionally. 108.162.216.118 05:56, 7 January 2018 (UTC)
This would all be OK if it were not for the fact that devious black-hat hackers can come up with devious ways to see the information that should have been discarded in the "path-not-taken". So even though the computer will eventually decide that some piece of information should not be accessible - you can find out the value it would hypothetically read - even though it will soon decide that it should not access the information.
The "rowhammer" problem is something entirely different. Computer memories are organized as a two-dimensional grid of rows and columns - and are physically constructed from tiny capacitors. If you apply just the RIGHT pattern of rapid changes to one row of the grid, you can cause one of the capacitors on the next row to incorrectly change state. This is a design flaw in the memory chip - and it allows (in some circumstances) programs to change data in memory locations that they have no right to change.
SteveBaker (talk) 19:33, 5 January 2018 (UTC)
uhhh did you just copy and paste your entire edit into talk? DPS2004'); DROP TABLE users;-- (talk) 20:19, 5 January 2018 (UTC)
- Pretty much. When I got here, there was no information about the comic at all. Since I'm unfamiliar with all of the other stuff that goes into an explain, I left it as a comment so someone else could use it...but after a while, nobody did, so I copy-pasted it into the explanation...with some tweaks! Sorry if that was a faux-pas of some variety! SteveBaker (talk) 21:53, 5 January 2018 (UTC)
What? Servers are vulnerable to actual hammers? Huh, do you suppose they're be vulnerable to an actual trolley as well? I have a spare server, does anyone have a spare trolley? ~~ SiliconWolf
- My server is actually mounted inside a trolley - precisely to avoid this kind of issue. SteveBaker (talk) 23:02, 5 January 2018 (UTC)
- I wouldn't recommend that. A collision would anger the honeybees. ~AgentMuffin
- Do you think we can put a quantum computer in a trolley and ask the ghost in the shell to chase down the one causing the above vulnerabilites? 141.101.69.87 11:05, 8 January 2018 (UTC)
The most helpful technical explanation I’ve found is here: https://www.raspberrypi.org/blog/why-raspberry-pi-isnt-vulnerable-to-spectre-or-meltdown/ ;the comments also provide useful clarification. PotatoGod (talk) 02:54, 6 January 2018 (UTC)
Could an explanation be added as to what a trolley is? Being in the UK, my first thought was that of a shopping trolley (US: Shopping cart). Over here, we call trollies "trams" 162.158.34.4 11:39, 6 January 2018 (UTC)
- The analogy is the same, just the speed and engine that changes. 162.158.74.9
- Actually, I find "trolley" to be a very UK word. Outside of this Trolley Problem I never hear it here in North America. Without looking it up, I would expect the mere name means it probably was thought up in the UK in the fist place, or by someone using UK English to name it. Only other term I can think of right now is "streetcar", but I never hear that either. Blanking on what they usually are called (perhaps "tram" as well), but they don't have any anymore in my city. This commonality of terms might be different in cities equipped with them. :) NiceGuy1 (talk) 04:09, 7 January 2018 (UTC)
I totally expected "Schrodinger's Cat's Cat" to be a popular meme, but apparently it is not. Google search I hereby claim it.These Are Not The Comments You Are Looking For (talk) 08:18, 7 January 2018 (UTC)
The explanation assumes Cueball is taking Ponytail's comment litteraly while she agrees with him because of the humor. To me it rather looked like Cueball was making a joke that Ponytail agreed to. The fact that he said "The Cloud" would confirm this view IMHO, as he deliberatly chose another metaphor to push the silly image even further. 141.101.69.87 11:05, 8 January 2018 (UTC)
- Cueball is speaking as a computer know-nothing. Hence, asking for such an explanation, and hence her explanation being in more layman's terms. This seems to indicate that his summation is his attempt to try to appear not ENTIRELY stupid and trying to weakly sum up her explanation - and use a buzzword he knows, "Cloud", to further sell the idea that he understands. To me, Ponytail agrees more as a form of "Ah, close enough. I don't feel like clarifying further, and this should be good enough to ensure proper caution.". His follow up includes elipses to indicate his actual uncertainty, as he gives the one preventative step he knows about: Installing updates. NiceGuy1 (talk) 06:22, 9 January 2018 (UTC)
- Thoughts by someone who just arrived
I just read the available explanation, and it seems fairly complete to me, someone who knew next to nothing about spectre and meltdown besides their names before reading. In my opinion, the 'something seems to be missing' tag can be removed. However, as I am no expert on the matter, I will leave someone else to decide and perform (or not perform) the action of removing it. 172.68.65.186 02:30, 8 January 2018 (UTC)
