Difference between revisions of "424: Security Holes"
(well, yes, correct; so move the explanation, so that it is visible what do those “//” mean in this comic) |
|||
| Line 8: | Line 8: | ||
==Explanation== | ==Explanation== | ||
| − | The “Debian-OpenSSL fiasco” was a major security problem discovered in the {{w|Debian}} {{w|Linux distribution}} and its version of the {{w|Cryptography|cryptographic}} library called {{w|OpenSSL}}. With just a tiny change in the software, which was intended to have no effect on security, its {{w|Random number generation|random number generator}} was completely crippled, as was the security of all cryptographic keys generated by the system. The problem was created when a Debian developer removed one line of code | + | The “Debian-OpenSSL fiasco” was a major security problem discovered in the {{w|Debian}} {{w|Linux distribution}} and its version of the {{w|Cryptography|cryptographic}} library called {{w|OpenSSL}}. With just a tiny change in the software, which was intended to have no effect on security, its {{w|Random number generation|random number generator}} was completely crippled, as was the security of all cryptographic keys generated by the system. The problem was created when a Debian developer removed one line of code which was crucial, even though it could seem like it did nothing useful. (More detail about the fiasco: [http://trailofbits.files.wordpress.com/2008/07/hope-08-openssl.pdf ''Crippling Crypto: The Debian OpenSSL Debacle''], [http://wiki.debian.org/SSLkeys Debian’s information page about the problem]) |
The title text refers also to this issue: After the security problem was found, all cryptographic keys generated or used on the broken operating system needed to be replaced. Many systems introduced special checks for such weak keys, adding the keys to {{w|Blacklisting|blacklists}}, thereby preventing their use and forcing users to create new keys. [[Randall]] was apparently affected by that when uploading this comic to the server. | The title text refers also to this issue: After the security problem was found, all cryptographic keys generated or used on the broken operating system needed to be replaced. Many systems introduced special checks for such weak keys, adding the keys to {{w|Blacklisting|blacklists}}, thereby preventing their use and forcing users to create new keys. [[Randall]] was apparently affected by that when uploading this comic to the server. | ||
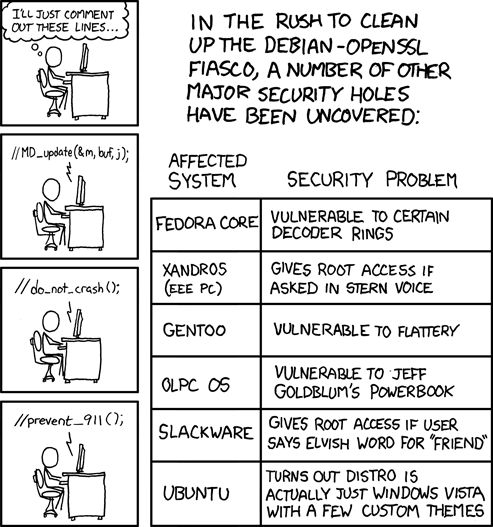
| − | The comics on the left presents Cueball as a programmer who, on a whim, removes pieces of code, presumably thinking they are not necessary. The first removed line, <code>MD_update(&m, buf, j);</code> is the exact piece of code which [http://svn.debian.org/viewsvn/pkg-openssl/openssl/trunk/rand/md_rand.c?rev=141&view=diff&r1=141&r2=140&p1=openssl/trunk/rand/md_rand.c&p2=/openssl/trunk/rand/md_rand.c was removed] in the Debian fiasco. The next panels show him commenting out fictitious lines of code apparently preventing bad things from happening. | + | The comics on the left presents Cueball as a programmer who, on a whim, removes pieces of code ({{w|Comment (computer programming)|commenting out}} the code by prepending the line with two slashes), presumably thinking they are not necessary. The first removed line, <code>MD_update(&m, buf, j);</code> is the exact piece of code which [http://svn.debian.org/viewsvn/pkg-openssl/openssl/trunk/rand/md_rand.c?rev=141&view=diff&r1=141&r2=140&p1=openssl/trunk/rand/md_rand.c&p2=/openssl/trunk/rand/md_rand.c was removed] in the Debian fiasco. The next panels show him commenting out fictitious lines of code apparently preventing bad things from happening. |
The other part of the comic lists “security problems” which were allegedly discovered in other Linux variants afterwards: | The other part of the comic lists “security problems” which were allegedly discovered in other Linux variants afterwards: | ||
Revision as of 10:50, 25 February 2013
| Security Holes |
 Title text: True story: I had to try several times to upload this comic because my ssh key was blacklisted. |
Explanation
The “Debian-OpenSSL fiasco” was a major security problem discovered in the Debian Linux distribution and its version of the cryptographic library called OpenSSL. With just a tiny change in the software, which was intended to have no effect on security, its random number generator was completely crippled, as was the security of all cryptographic keys generated by the system. The problem was created when a Debian developer removed one line of code which was crucial, even though it could seem like it did nothing useful. (More detail about the fiasco: Crippling Crypto: The Debian OpenSSL Debacle, Debian’s information page about the problem)
The title text refers also to this issue: After the security problem was found, all cryptographic keys generated or used on the broken operating system needed to be replaced. Many systems introduced special checks for such weak keys, adding the keys to blacklists, thereby preventing their use and forcing users to create new keys. Randall was apparently affected by that when uploading this comic to the server.
The comics on the left presents Cueball as a programmer who, on a whim, removes pieces of code (commenting out the code by prepending the line with two slashes), presumably thinking they are not necessary. The first removed line, MD_update(&m, buf, j); is the exact piece of code which was removed in the Debian fiasco. The next panels show him commenting out fictitious lines of code apparently preventing bad things from happening.
The other part of the comic lists “security problems” which were allegedly discovered in other Linux variants afterwards:
Cryptographic software in Fedora Core was allegedly not secure against toy decoder rings. Xandros (used in Asus Eee PC netbooks) gave superuser privileges to anybody “if asked in a stern voice”. Gentoo would succumb to flattery.
OLPC OS could have been attacked using Jeff Goldblum’s notebook, which refers to a scene in the Independence Day movie, where Jeff Goldblum’s character was able to hack into an alien spaceship using his Apple PowerBook computer (which is a topic of great contempt by geeks who point to the absurdity of such a construction).
Slackware gave superuser privileges to anybody who “says Elvish word for ‘friend’”, which refers to a scene in The Lord of the Rings, where the entrace door to Moria could have been opened using a password mellon, the Elvish word for “friend”, as indicated on the door itself.
And Ubuntu, which is another Linux distribution, was allegedly found to be actually Windows Vista (Microsoft Windows being a direct competitor to Linux) with a different graphics.
Transcript
- [Man sitting at computer] I’ll just comment out these lines...
// MD_update(&m, buf, j);
// do_not_crash();
// prevent_911();
- In the rush to clean up the debian-openssl fiasco, a number of other major security holes have been uncovered:
Affected system Security problem Fedora Core Vulnerable to certain decoder rings Xandros (EEE PC) Gives root access if asked in a stern voice Gentoo Vulnerable to flattery OLPC OS Vulnerable to Jeff Goldblum’s Powerbook Slackware Gives root access if user says Elvish word for “friend” Ubuntu Turns out distro is actually just Windows Vista with a few custom Themes
Discussion
Could the Slackware one imply that harder nerds/geeks are more fond of this specific Linux distro? 108.162.212.196 01:00, 4 December 2013 (UTC)
Perhaps he's also implying aliens use OLPC? 108.162.216.45 (talk) (please sign your comments with ~~~~)
I think the Xandros/EEE PC vulnerability "gives access if asked in a stern voice" is a reference to comic 413: New Pet, where Cueball and Megan made a pet out of a EEE PC on wheels inside a hamster ball. Pets sometimes need to be talked to sternly if they're unwilling to obey commands; in this case, a EEE PC needs to be talked to sternly in order to give the commander root access. Codefreak5 (talk) 21:36, 15 July 2014 (UTC)
- I like to think teh "exploit" is just
sudo sudo [arbitrary command]. AzureArmageddon 15:40, 1 October 2023 (UTC)
The Gentoo explanation does not make sense. Gentoos succumbing to flattery should mean the users use flattery on the Gentoo, not the other way around. --flewk (talk) 16:43, 28 December 2015 (UTC)
Crippling Crypto (the first article mentioned as offering more detail on the Debian-OpenSSL vulnerability) analogises the resulting problem by partly reproducing 221: Random Number. Should this be mentioned in this article or in 221, or both, or not mentioned in either? 108.162.250.87 09:39, 30 November 2020 (UTC)
This has aged interestingly, given that about half of those security problems are legitimate weaknesses of current LLM AI models. Not the same as operating systems, of course, but you'd be terrified by how much people already trust them to be secure.172.71.183.72 12:00, 25 March 2024 (UTC)
