Difference between revisions of "177: Alice and Bob"
(→Explanation) |
|||
| Line 22: | Line 22: | ||
The title text continues the theme of Randall getting barred from speaking at conferences due to his unusual take on certain topics. | The title text continues the theme of Randall getting barred from speaking at conferences due to his unusual take on certain topics. | ||
| − | To further spice things up, there are many other characters in the Alice/Bob canon, including Mallory, the ''mal''icious, who wants to actually ''alter'' the message with nefarious intent; Craig, the ''cr''acker, who doesn't particularly care about the message but ''does'' care about the passwords used; and Chuck, a third party in the communication who secretly has a villainous intent. | + | To further spice things up, there are many other characters in the Alice/Bob canon, including Mallory, the ''mal''icious, who wants to actually ''alter'' the message with nefarious intent; Craig, the ''cr''acker, who doesn't particularly care about the message but ''does'' care about the passwords used; plod, a law enforcement officer attempting to access key or data, and Chuck, a third party in the communication who secretly has a villainous intent. |
==Transcript== | ==Transcript== | ||
Revision as of 16:25, 4 July 2013
| Alice and Bob |
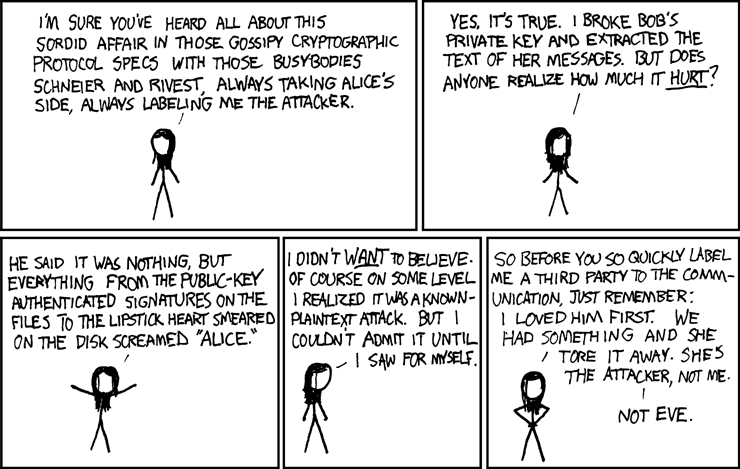 Title text: Yet one more reason I'm barred from speaking at crypto conferences. |
Explanation
Any good cryptography presentation will include at least one story about Alice and Bob. They are the canonical "protagonists" of the crypto world, frequently used in illustrations to demonstrate how a cryptographic system works. (The names were mostly chosen to abbreviate to A and B.)
Here, Randall casts the story in a different light. Instead of Alice and Bob being perfectly innocent people who just want to communicate in private, Bob is actually having an affair with Alice, and his former partner, upset, cracked the encryption to see what the message contained. Nevertheless, the "gossipy cryptographic protocol specs" all took Alice's side (since the goal of any good crypto system is, of course, to succeed in this struggle).
The rest of the comic makes a few other allusions to cryptography:
- Bruce Schneier and Ron Rivest are two well-known cryptographers. They have written lots of papers that use Alice and Bob as examples (Alice / Bob fanfic, if you will).
- Public and private keys are two extremely large numbers, chosen such that there's a mathematical relation between them, and yet it's extremely hard (i.e. would take many billions of years) to derive the private key from the public key. They're the basis of asymmetric cryptography. A public-key authenticated signature is a way of cryptographically proving that a certain person created a file, as only that person could have possibly generated that signature. One downside is that anybody who has the public key can verify who a message is from, so it removes plausible deniability; Bob's partner clearly knew that Alice and Bob were communicating, on disks marked by lipstick hearts no less.
- A known-plaintext attack is a type of cryptographic attack where the plaintext (i.e. unencrypted text) of a message is known, and the attacker wants to figure out the keys used to encrypt the message. The woman is saying that she should have known all along that the messages were adulterous in nature.
Finally, in a twist ending, the girlfriend is revealed to be none other than Eve, the eavesdropper, who is also ubiquitous in Alice and Bob stories. Hell hath no fury, indeed.
The title text continues the theme of Randall getting barred from speaking at conferences due to his unusual take on certain topics.
To further spice things up, there are many other characters in the Alice/Bob canon, including Mallory, the malicious, who wants to actually alter the message with nefarious intent; Craig, the cracker, who doesn't particularly care about the message but does care about the passwords used; plod, a law enforcement officer attempting to access key or data, and Chuck, a third party in the communication who secretly has a villainous intent.
Transcript
- [Eve stands in the frame, talking to the reader.]
- Eve: I'm sure you've heard all about this sordid affair in those gossipy cryptographic protocol specs with those busybodies Schneier and Rivest, always taking Alice's side, always labeling me the attacker.
- Eve: Yes, it's true. I broke Bob's private key and extracted the text of her messages. But does anyone realize how much it hurt?
- Eve: He said it was nothing, but everything from the public-key authenticated signatures on the files to the lipstick heart smeared on the disk screamed "Alice."
- Eve: I didn't want to believe. Of course on some level I realized it was a known-plaintext attack. But I couldn't admit it until I saw it for myself.
- [Eve places her hands on her hips.]
- Eve: So before you so quickly label me a third party to the communication, just remember: I loved him first. We had something and she tore it away. She's the attacker, not me. Not Eve.
Discussion
This part: "but everything from the public-key authenticated signatures on the files to the lipstick heart smeared on the disk screamed "Alice." " reminds me of the song Alice by Tom Waits. May or may not be intentional. 108.162.242.120 18:10, 26 November 2013 (UTC)
The title text refers to comic 153, the first time Randall claimes to be banned from a conference (others to follow, e.g. comics 463 and 541). And I don't consider this comic to have a "twist ending" revealing that it's Eve talking. She says that she is commonly being labelled the attacker in the very first panel. --YMS (talk) 15:37, 12 January 2014 (UTC)
Is Danish's name actually Eve? They seem to look the same, and have the same character. 108.162.246.5 17:51, 28 January 2014 (UTC)
Would that make Black Hat Bob? And who would be Alice? 173.245.55.76 02:30, 17 March 2014 (UTC)
None of them because they aren't the same characters! -Pennpenn 108.162.250.162 00:18, 16 July 2015 (UTC)
In addition to the obvious cryptography naming convention, I thought there was a reference to the 1969 movie classic Bob&Carol&Ted&Alice about infidelity and partners swapping. The climax scene has all 4 climb to bed together with Bob and Alice (married, but not to each other) kissing passionately. The movie inspired a genre of sexual comedies, and to this day, calling out a few of the names with a "&" between is used as a euphemism for "too sexually liberal for their own good." Mountain Hikes (talk) 16:13, 19 September 2015 (UTC)
- Isn't she Danish?
She looks very similar to the character called Danish after an enigmatic remark in 515. But here she is called Eve. Shouldn't we rename the character everywhere? 162.158.102.137 13:39, 12 March 2016 (UTC)
Hmm... the existance of http://aram.xkcd.com/ suggests that Black Hat Guy has the same name as his acknowleged inspiration, so does that make them Aram and Eve ;) ? -- 141.101.98.142 10:07, 8 January 2017 (UTC)
Is "barred" used meaning "banned" or is that a typo exposing Randall as a Dvorak typist? --Volemo (talk) 23:12, 29 October 2023 (UTC)
- "Prevented, either by a physical barrier or by conditions." Yup. 172.69.79.143 23:38, 29 October 2023 (UTC)
 Add comment
Add comment
