1820: Security Advice
| Security Advice |
 Title text: Never give your password or bank account number to anyone who doesn't have a blue check mark next to their name. |
Explanation
| |
This explanation may be incomplete or incorrect: Incomplete. TBD:Complete tip explanations Do NOT delete this tag too soon. If you can address this issue, please edit the page! Thanks. |
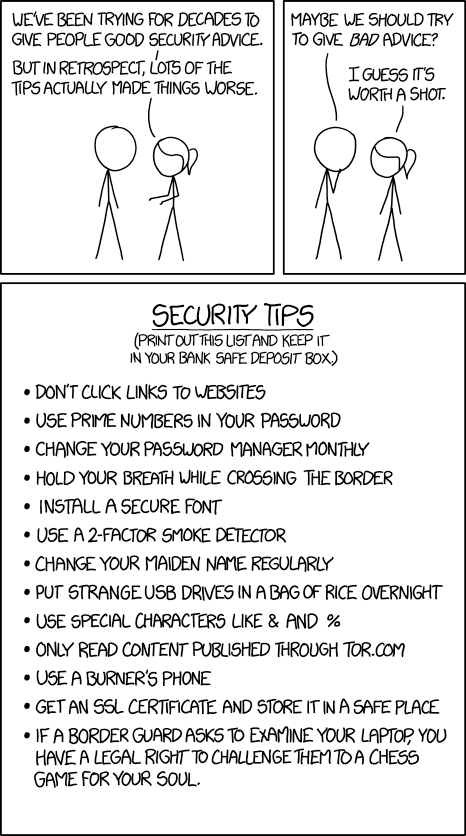
The comic depicts a conversation between Cueball and Ponytail, discussing the fact that giving people security advice has failed to improve their internet security, and in some cases even made things worse (such as requiring complicated passwords leading to people leaving post-it notes with their passwords on their screen, leading to huge security risks). As a result Cueball suggests giving bad advice instead, in hopes of a positive effect. The last panel contains a list these security tips, which are parodies of actual security tips.
The last tip on the image is most likely a reference to Ingmar Bergman's film The Seventh Seal.
Security Tip Explanations
| Security Tip | Explanation |
|---|---|
| Don't click links to websites | The usual tip is "Don't click on suspicious website links." The comic's variation instead implies don't click on any links to any websites, or don't use the internet. |
| Use prime numbers in your password | |
| Change your password manager monthly | |
| Hold your breath while crossing the border | This in its self, wouldn't do anything, but if you hold your breath for too long you could pass out when crossing, or look stressed/suspicious. Overall, this would not help you. |
| Install a secure font | |
| Use a 2-factor smoke detector | A new way to keep accounts secure is 2-factor authentication, which usually means you enter your password, and then look for an email (or go into a mobile app) with a code which you then enter into the website. A 2-factor smoke detector would be useless, because it would require you to verify that there is actually a fire with a code, when the purpose of smoke detectors are to warn you about fires you don't know about. |
| Change your maiden name regularly | A common security question (a type of 2-factor authentication from the previous tip) asks you for your maiden name. |
| Put strange USB drives in a bag of rice overnight | The usual security tip is "Don't plug strange USB drives into your computer," because sometimes attackers put viruses that infect your system when plugged in. This tip implies that you should "put USB drives in a bag of rice overnight" which is a common technique for drying out water damaged devices, due to rice's absorbent qualities. This would not clean the drive of viruses, and unless the drive was wet (perhaps because you found it outside due to it being called "strange") it would not do anything. |
| Use special characters like & and % | |
| Only read content published through Tor.com | |
| Use a burner's phone | |
| Get an SSL certificate and store it in a safe place | |
| If a border guard asks to examine your laptop, you have a legal right to challenge them to a chess game for your soul. | This tip is likely a reference to Ingmar Bergman's film The Seventh Seal |
| Never give your password or bank account number to anyone who doesn't have a blue check mark next to their name. (Title Text) |
Transcript
| |
This transcript is incomplete. Please help editing it! Thanks. |
- Ponytail: We've been trying for decades to give people good security advice.
- Ponytail: But in retrospect, lots of the tips actually made things worse.
- Cueball: Maybe we should try to give bad advice?
- Ponytail: I guess it's worth a shot.
- Security tips
- (Print out this list and keep it in your bank safe deposit box.)
- Don't click links to websites
- Use prime numbers in your password
- Change your password manager monthly
- Hold your breath while crossing the border
- Install a secure font
- User a 2-factor smoke detector
- Change your maiden name regularly
- Put strange USB drives in a bag of rice overnight
- Use special characters like & and %
- Only read content published through Tor.com
- Use a burner's phone
- Get an SSL certificate and store it in a safe place
- If a border guard asks to examine your laptop, you have a legal right to challenge them to a chess game for your soul.
Discussion
Secret questions are not 2-factor authentication (2FA). They are just a really shitty password, something that you know. --JakubNarebski (talk) 14:33, 5 April 2017 (UTC)
Secret questions are more like 0-factor authentication, since they typically ask for public data. Shirluban 141.101.88.106 14:39, 5 April 2017 (UTC)
Even when it isn't public it is often very unsecure - like: "your password has to have upper and lower case letters, numbers" and other requirements - if you forget it just enter the brand of your first car, there are about 20 likely answers (make it 40 if you need to additionally see wether or not it has been capitalized) 162.158.92.46 15:18, 5 April 2017 (UTC)
Use prime numbers in your password: this would only limit the number of possible passwords for a hacker to check.
Use special characters like & and % : this advice is thoroughly handled in https://xkcd.com/936/ Changing characters into a special one does adds just very little to the search space. However, a video from Computerphile suggests inserting a random character somewhere in the password which might actually be rather helpful
162.158.111.211 14:53, 5 April 2017 (UTC)
- Note that if you replace any number n with the n-th prime number the security of your password would be really better. So would the length, of course. -- Hkmaly (talk) 23:44, 7 April 2017 (UTC)
Maybe you really should use a secure font Font related bug 162.158.79.161 15:13, 5 April 2017 (UTC)
Should the blue check mark tip be noted as only being useful on Twitter? Usually, the advice doesn't apply to emails, which are significantly more likely to ask for your less-secret account details, but also significantly less likely to have a blue check mark. 162.158.2.10 15:15, 5 April 2017 (UTC)
"If a border guard asks to examine your laptop, you have a legal right to challenge them to a chess game for your soul.", do any of you know exactly what is the original advice here? This is probably different in different countries, but if I recall correctly you can't prevent them from seizing your device, but you are not required to provide them your passwords (but they may give you a hard time or deny your entry if you are not a citizen). Anyone can confirm this? 108.162.216.22 15:16, 5 April 2017 (UTC)
- In the UK, police can demand your password if they suspect a crime, and border staff can demand your password even without permission. People can be - and have been - imprisoned for not providing a password. Cosmogoblin (talk) 23:39, 15 August 2018 (UTC)
The rice trick doesn't even work for wet phones. http://www.gazelle.com/thehorn/wp-content/uploads/2014/05/Water-Damage-Prevention-and-Recovery.pdf 162.158.111.211 15:33, 5 April 2017 (UTC)
- Yeah - beat me to it! The rice trick doesn't work...not for phones or anything else for that matter. So this is double bad advice. 162.158.69.39 16:06, 5 April 2017 (UTC)
- As someone who has worked with electronics, educated in electronics design, I find the most effective solution is to remove all power as quickly as possible - unplug it and remove the battery - then let it dry out. Liquid damages by allowing electricity to take paths it shouldn't. No power, no problem. Which is why I don't and will never trust any device which doesn't allow you to quickly pop out the battery (iPads and many iPhones, for example). No battery pull means risk to me. - NiceGuy1 108.162.219.88 07:20, 7 April 2017 (UTC) I finally signed up! This comment is mine. NiceGuy1 (talk) 05:07, 13 June 2017 (UTC)
Border guard - I'd like to see a bit more explanation, please, on how Ingmar Berman's film shows a man playing chess with Death, and possibly the infamous subversion of this trope in Bill And Ted's Bogus Journey. As it is, the explanation is only the bare bones. --172.68.34.52 17:35, 5 April 2017 (UTC)
Checking the padlock icon in your browser is not enough to make sure you're really connected to the site you think. You have to check the domain too, to make sure you're not on a typosquatter domain (e.g. explianxkcd.com instead of explainxkcd.com). For really important thing like banking, you should check for an Extended Validation Certificate (Firefox shows the name of the organization running the website beside the padlock to indicate an EV-Certificate). This means, that the CA checked if the website operator really is who he pretends to be (and take a hefty sum of money for the process). Yeah, i know, security isn't easy. Using the brain still can't be replaced. --162.158.202.160 20:14, 5 April 2017 (UTC)
- Extended Validation Certificate means that the CA SHOULD have checked ... Symantec for example didn't (and Google is punishing them for it). -- Hkmaly (talk) 23:44, 7 April 2017 (UTC)
These two characters are often disallowed in passwords because of their relevance to SQL (a common database query language). A badly written security system using SQL could have severe bugs (and vulnerabilities) if these characters were used in a password. So instead of fixing the bugs, users are kindly requested/forbidden to use & and % because that would break the system? Relying on empathy instead of fixing the problem, similar to "please don't break in, we're too poor to afford a decent lock". Sounds like Black Hat in a role as security advisor could come up with. 162.158.111.211 21:01, 5 April 2017 (UTC)
- I once saw a funny notification at a login screen. It read: "Only log on if you are an authorized user". Hilarious... Elektrizikekswerk (talk) 13:03, 6 April 2017 (UTC)
- In reverse, for work I'm supposed to come up with a 2-factor authorization method. A simple password is one factor. I thought the second factor was easy: you also need physical access to a computer in the network. Apparently that's not "technical" enough or something, external advisors tell us that the fact that a hacker needs to physically break in to hack the system doesn't count as a second factor. (if anyone can point to an authority saying that it does I'd be very happy!) 162.158.111.211 00:27, 7 April 2017 (UTC)
- I once saw a funny notification at a login screen. It read: "Only log on if you are an authorized user". Hilarious... Elektrizikekswerk (talk) 13:03, 6 April 2017 (UTC)
"Turing-complete kerning specification language in OpenType fonts" needs a citation. Is this just referring to the TeX language in general?
"the US banking system, where there is very little security for direct account drafts, and because of that it is advised there to keep the account number as secret as possible. In contrast, in Europe..." also needs citation. Why is giving out your bank account number more secure in Europe? I googled around a bit but couldn't find any verification of this (aside from discussions on chips vs. magnetic strips, which is a different issue). --Tractarian (talk) 17:29, 6 April 2017 (UTC)
From experience, here in the UK, if I wanted someone to transfer money to me online, I just give them my account number and routing (or "sort") code. People even publish this information on websites.
Specifically, a lot of the rules here place liability on the banks for fraudulent and unauthorised transactions as long as the consumer wasn't careless or breached the rules of their account.
See https://www.directdebit.co.uk/DirectDebitExplained/pages/directdebitguarantee.aspx https://www.chequeandcredit.co.uk/information-hub/faqs/cheque-fraud
But I can't imagine how anyone could initiate a transaction from my account without forging a document or hacking my online banking details (for electronic transfers).--162.158.111.37 19:33, 6 April 2017 (UTC)
- Yeah from my, Dutch, view that part also seems strange. Like "I'm not telling you my e-mail address so you can't read my e-mail". Also, anyone you ever sent money to gets to know your account number don't they? After that, can they just walk into a bank saying "Hi I'm John, account number 12345, give me $5000 please"? I'd like a comic showing my accountnumber to test how I'd be hurt by telling the whole world :) It gets stranger, in order to get a refund to my credit card I not only had to give my credit card number but the expiry date as well. I always considered the expiry date as a very simple password to prove you have the card itself. This felt more like "You wouldn't want total strangers to put money on your account, would you?" (thinking about it, maybe it's used as a "checksum"). 162.158.111.211 22:35, 6 April 2017 (UTC)
- As a North American, around here it seems like allowing someone to know your account number potentially gives a thief a target. If they manage to somehow hack their way into your bank, they now know a valid account number to aim for. Much less suspicious than trying their luck with picking one at random. Also, when we transfer money to each other, the account number doesn't enter into it. I go to my bank's website, start an e-Transfer, and tell it to send X dollars to this email account, and I add a security question - "What's my favourite online comic?" - and the answer - "xkcd". They get the email, select what bank they want to deposit the money to (and login to their bank's website), then give the arranged or known answer to my question. Our account numbers are only used / shared with our own respective banks. - NiceGuy1 108.162.219.88 07:20, 7 April 2017 (UTC) I finally signed up! This comment is mine. NiceGuy1 (talk) 05:07, 13 June 2017 (UTC)
- There is nothing secure on credit card. Even the Card Security Code number is only protected by people not being allowed to store it in database. Yeah I'm sure thieves would comply with this rule. And that e-Transfer ... so, if someone intercepts that email and tells the bank it come to his email address, the bank would send the money to him? Doesn't seem safe either ; email is very insecure way to exchange data. -- Hkmaly (talk) 23:44, 7 April 2017 (UTC)
- As a North American, around here it seems like allowing someone to know your account number potentially gives a thief a target. If they manage to somehow hack their way into your bank, they now know a valid account number to aim for. Much less suspicious than trying their luck with picking one at random. Also, when we transfer money to each other, the account number doesn't enter into it. I go to my bank's website, start an e-Transfer, and tell it to send X dollars to this email account, and I add a security question - "What's my favourite online comic?" - and the answer - "xkcd". They get the email, select what bank they want to deposit the money to (and login to their bank's website), then give the arranged or known answer to my question. Our account numbers are only used / shared with our own respective banks. - NiceGuy1 108.162.219.88 07:20, 7 April 2017 (UTC) I finally signed up! This comment is mine. NiceGuy1 (talk) 05:07, 13 June 2017 (UTC)
- That's why these days even credit cards have PIN numbers. And actually, e-Transfers are one of the most secure things I take part in. On both sides of the transfer (i.e. both me and the person I'm paying) we each individually have to have a login setup with our banks, one which uses our bank card number and/or account number (hence part of the reason for a North American's aversion to letting anybody know what it is), and which includes a password like any other login. So, for a person to steal money from me by transfering it out of my account, they'd need my login name (if my bank uses one) or card number or account number - whatever the bank uses to figure out who you are online, plus having to know which one they need to know. The thief can't just set up a new login attached to my account, because I already have one, and banks don't allow a duplicate account. They would also need my password. And for a person to intercept my transfer, in addition to all that (for my recipient this time) they'd also have to intercept the email - which my recipient knows to expect, usually within minutes of when the email will arrive - but also they would need to know the answer to the question I set, which would usually be information you only share with the recipient. I'm reminded of Harry Potter And The Half-Blood Prince, where for security all good people came up with personal security questions to confirm each-others identities. In this case it can be as simple as "Where am I right now?", which you would have discussed when arranging payment, or "Where did we meet?" or "What teacher did we both have?", stuff like that. - NiceGuy1 162.158.126.76 05:53, 12 April 2017 (UTC) Mine too! NiceGuy1 (talk) 05:07, 13 June 2017 (UTC)
- In the UK in 2008, the UK government lost 25 million sets of bank account details (on two unencrypted CDs sent through the post - this kind of data breach is a common pastime of UK government departments). Jeremy Clarkson claimed there was no security problem, and to prove it, he published his bank account and sort code. Within days somebody had donated £500 from his account to Diabetes UK. Cosmogoblin (talk) 16:07, 22 July 2018 (UTC)
"Don't click links to web sites"
Because it is trivial to have a link display "schmoo.com" but actually send you to "dastardlyevil.com" when clicked, this is actually usable advice. If the link displays an website address, one that is correct, highlight and copy the text and paste it directly into a browser's address bar. Barring that, right click on the link, copy the hidden link address, and paste that into the address bar. Of course then you should check carefully that the copied address isn't bougus. These Are Not The Comments You Are Looking For (talk) 00:49, 9 April 2017 (UTC)
- Usually, any software I use will show the real address in the status bar when I hover the mouse over the link. I always check if these match, and if so, I know I can feel free to click (assuming said agreeing address is one I wish to visit, of course, LOL!) - NiceGuy1 162.158.126.76 05:53, 12 April 2017 (UTC) I finally signed up! This comment is mine. NiceGuy1 (talk) 05:07, 13 June 2017 (UTC)
- I go further - if I'm at all suspicious of a link I'll type it directly. Copy-paste will retain homoglyphs, characters which look similar but aren't; for example explainxkcd.com is correct, but eхplainхkcd.com is not (using the Cyrillic HA in place of the Latin x), and could be registered as an entirely different website. Cosmogoblin (talk) 16:16, 22 July 2018 (UTC)
"If the smoke detector worked according to the authentication logic it will be less likely to detect smoke, effectively lessening fire safety as compared to a single sensor one"
It'll be less likely to detect fire, but that does not necessarily mean lesser safety. There is a possibility of a "fire alarm that cried wolf" syndrome. If there is ever a real emergency, you really don't want people think "it's probably just another smoking toaster, I have time to take a quick shower and brush my teeth before I leave". --172.68.54.52 08:04, 9 April 2017 (UTC)
- The point here is not more safety but fewer false alarms. Similarly in rooms were you have "smoke" regularly you might either install a detector that doesn't scan for smoke but instead for heat or infrared light or you might install two smoke detectors in the far corners of a larger room, that only give an alarm if they both detect smoke. --162.158.90.126 13:28, 9 April 2017 (UTC)
- In a two-alarm system like that, you could have a small fire break out close to one detector that, by the time it has created enough smoke to trigger the far detector and start the alarm, has grown to the point that it has now become difficult to fight, and at the very least has caused considerable damage which could have been prevented if only the first detector had "spoken up" immediately. A system that second-guesses itself is NOT good. - NiceGuy1 162.158.126.76 05:53, 12 April 2017 (UTC) I finally signed up! This comment is mine. NiceGuy1 (talk) 05:07, 13 June 2017 (UTC)
Fourth amendment does not apply to border or customs searches
See border search exception: https://en.m.wikipedia.org/wiki/Border_search_exception
In fact we don't need the entire paragraph about the fourth amendment.
- Use a burner's phone
While it's possible that "burner" could refer to someone who attends the Burning Man festival, I believe it's more likely this is referring to someone who smokes marijuana, which is a common term in popular informal English. This also makes a nice connection with the part about typical usage of burner phones by drug dealers. --Ianrbibtitlht (talk) 14:11, 8 June 2017 (UTC)
- Agreed. I feel like there's no question, Randall is referring to a pot smoker, i doubt there was ever any intent by him to reference Burning Man here. NiceGuy1 (talk) 05:24, 13 June 2017 (UTC)
The tip in the title text isn’t technically wrong, just misleading, as you shouldn’t give you passwords or bank info to people without blue checkmarks. You also shouldn’t give them to people with blue checkmarks either, of course, but that doesn’t make the tip wrong. PotatoGod (talk) 15:44, 10 August 2018 (UTC)
did something happen to this page? i can't remove them either. JLZ0kTC5 (talk) 01:49, 24 July 2023 (UTC)
