2677: Two Key System
| Two Key System |
 Title text: Our company can be your one-stop shop for decentralization. |
Explanation[edit]
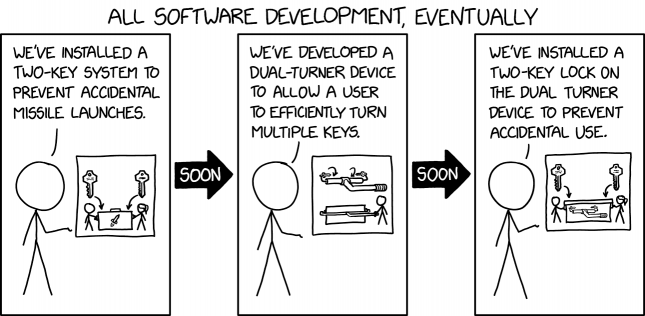
As an allegory, the comic relates the results of software development to the reputed safeguards of nuclear missile launch systems. Such precautions include the need for two independent operators for authorization, to prevent honest mistakes or the rogue actions of lone-actors. This is the kind of procedure used at a launch site where two duty officers each need to turn their respective keys simultaneously. The physical distance between the keys ensures that an individual cannot turn both keys simultaneously, or initiate the sequence without the second person.
In relation to software development, the inconvenience caused by such precautions (like account passwords and two-factor authentication) has prompted the development of methods to make the process easier (like autofilling passwords or website cookies keeping a user logged in for multiple visits). Similarly, the system in the comic is made more convenient by using a dual key-turner that circumvents the need for two users to turn the keys.
And thus we find out that the thing used to make the safeguards less of a nuisance actually defeats the purpose of the safeguards. As with website passwords, where the use of a computer or device by someone else could allow them to use the autologin capabilities, or even to view all passwords used locally and take away for their own use, the whole point of the deliberately included security factor has been negated. It was only the perceived need for two independent operators that created the initial situation of requiring two separated keys, or indeed any keys at all!
Hence, after a further cycle of development, in order to restore the security of the two-key system, the two-key turning device (rather than being removed or made unworkable) is provided for use but only if it can be removed from a secure cabinet (labelled as giving access to the 'key turner', much as the original unit was labelled as giving access to a missile) with the requirements to open it being… two separate keys to be used at the same time! This could be seen as the same as password managers being introduced, either as a part of a browser or third-party add-ons, which automatically provide the user's passwords for any given access attempt but only when they are given a password (or other security factor) themselves. Rather than removing a 'problem', a new safeguard is added which does the exact same thing as the original, the possible nuisance (but hopefully also the necessary element of security) included.
Password management, as a process, is substantially similar to key management: Common failure-modes for both passwords and keys, include forgetting your own long-term passwords (especially if you changed computers after asking your computer to remember your passwords for you) which is functionally similar to misplacing your keys, or tending to use just a single password or key for every lock (which, if ever compromised in one situation, may lead to being compromised across many others). A Password Manager can reduce such issues, as it can be capable of 'spitting out' or transfering login details at will and letting you use many different passwords (even generating and using the kinds of passwords nobody should be able to guess, or remember!) across your many different websites, etc. But this passkey storage must itself be secure, and so should be functionally accessible perhaps only through use of a 'master passkey' or some other kind of authentication process, which may be subject to the same issues of forgetting, copying, or theft. Similarly, a central lockbox full of keys (such as those used at some car dealerships), can make handling multiple keys much easier, while introducing a single point of failure in the event that lockbox is illicitly accessed. Various forms of multi-factor authentication, plus auxiliary authentication methods for password recovery/reset, go some way to alleviate these challenges, at the expense of further intermediary steps and hardware requirements; but the balance between ease of use and security is never quite so simple and universal.
The title text mentions a one-stop-shop for decentralization. The drive to make use of "one-stop-shops" (such as a website aggregating searches for the best insurance) and also to decentralize (in this case not relying upon any one vendor, even that single aggregator who might actually not be the best aggregator) is another self-contradiction — because a one-stop-shop is by definition centralized.
The comic being posted on September 26th may or may not be a reference to Stanislav Petrov correctly rejecting the false detection of an incoming nuclear missile strike from the US on September 26th, 1983. When asked whether or not this reference was intentional, Randall has continuously declined to comment. 2052: Stanislav Petrov Day
For a related xkcd on security and software cycles, see 2044: Sandboxing Cycle.
Transcript[edit]
- [Caption above the panel:]
- All software development, eventually
- [Cueball is talking, while pointing to a drawing. It represents two keys, pointing to Cueball and Ponytail turning keys at either end of a missile launch system - a large anonymous cabinet except for a picture of a missile upon it]
- Cueball: We've installed a two-key system to prevent accidental missile launches.
- [An arrow is pointing to the next panel:] Soon
- [The drawing now represents a device with two inward-facing keys connected by a long bar with a further handle, and below that is shown how it is used with a cabinet such as above to let Cueball to activate the unit by himself]
- Cueball: We've developed a dual-turner device to allow a user to efficiently turn multiple keys.
- [An arrow is pointing to the next panel:] Soon
- [The drawing now represents two keys, pointing to Cueball and Ponytail turning keys at either end of a large similarly anonymous cabinet, except for the picture upon it being of the device of panel 2]
- Cueball: We've installed a two-key lock on the dual-turner device to prevent accidental use.
Discussion
Ah, for many long moments, I thought the "dual-key-turner" was a "dual-key-cutter" (but that it was a silly implemention, anti-parallel coaxial positioning of key blanks needs a complicated (pantograph?) cutting-heads system, more so than with parallel and adjacent blanks of any number). But now I'm on the right track and I laugh at the correct joke, and can think of any number of developments in safe (as in not 'forgotten') and secure (as in not misappropriated) password use that went into and out of the various "convenience for user"/"security for systems" modes, often mutually exclusive to the other mode. 172.70.90.61 15:33, 26 September 2022 (UTC)
I've long been annoyed that I can't use password auto-fill on Chrome's online password manager webpage. Barmar (talk) 16:36, 26 September 2022 (UTC)
Do you remember how banks were all "two-factor authentication" when we used to access them from computer and made us use the phone for confirmation? And how they don't seem to mind now when the bank can be completely controlled just from the (smart)phone? -- Hkmaly (talk) 20:35, 26 September 2022 (UTC)
Although I think this extends well beyond 'merely' "passwords" (in all their forms and combinations, from PINs to fingerprints!) I've taken the general feeling so far seen here in Talk and bulked up the explanation with the allegorical connections that might be the source of inspiration for the comic. And if you gave me the time to do it, I'd put an awful lot more (strange, really, I was often tired of rewriting SOPs to reflect the latest best-practices in 2FA/3FA when that was actually a big part of my job! "What you know/What you have/What you are"...) and without skipping over huge chunks. But (even if some bits get cut back down again) I think I've added value and maybe some narrative flow to the initial explanation, which was ok but perhaps not even how I would have arranged it (having then tried to preserve that skeleton arrangement of ideas). Darnit, I now sound full of myself. That's just me winding down from a big hot-edit that maybe even was too big, and anxiously awaiting someone else doing an even better total-rewrite/summary, regardless of what I just splurged there... ;) ((But, to clarify, the comic never mentions passwords. Highly likely it is (keys!) but it could be more wider ranging development issues. I'm sure I'll understand the moment someone clues me in on some other scope that this might actually reference.)) 172.70.90.245 22:00, 26 September 2022 (UTC)
Just to add something 'from the old days' (n.b., probably still applies to many non-web server logins, just rarer in more ubiquitous weblogins) is that any system that forces users to regularly change their passwords also tended to encourage the use of "Password1", "Password2", "Password3", sequentially (well, at least then you had a recent password to refresh in your mind), as they at least disallowed the immediate reuse of the last current password to replace itself, and possibly 'remembered' a number of past incarnations. But you tend not to get that feature (forced change/no reuse) on much of the modern infrastructure. It tends to focus more on a general form ("use special characters/uppercase!", as well as minimum lengths), which doesn't preclude bad 'sequential' practices (if you're even needing to do that) if you get ever "g!b³riZh1", "g!b³riZh2", "g!b³riZh3" started, then compromised by whatever means or reason... 172.70.85.49 22:45, 26 September 2022 (UTC)
"This could also be something of a reference to ‘two factor authentication’ a security annoyance which also requires ‘two keys’ (typically something from a dynamic physical token, as well as the static password which is susceptible to unauthorised reuse) that was adopted by more secure websites." - a stretch too far, IMO. This is a situation that has never gone from 'two keys' to 'one key (operator)' and back to 'two keys'. If anything, it might have been 2FA(password + token)->2FA(browser/password-manager + token), or even 1FA(password)->1FA(browser/whatever)->2FA( +token) for the slower/earlier adopters who had not originally worked out the token element. I've commented it out, because it isn't a good enough fit to really fit the analogy presented. Unless one of the other experts here can radically fix it to do so.
I don't personally use third-party PMs (either it's safe enough to just let the browser manage it, for convenience, or I actually remember all the individual passwords for things and untick any "Save password?" suggestion it gives me) so I also don't know how much 2FA is built into them in order to authorise them to "dual-key turn" (or if they even turn more than the one key, in any logical way), if you don't count the use of the installed PM itself as a virtual "possession" factor somehow. And I don't bank online, because I've never seen the advantages outweigh the potential problems. 162.158.159.19 18:51, 27 September 2022 (UTC)
With regard more specifically to software development, I think you'll find parallels with being able to run code (or, put another way, separating code from data). Once multi-user systems became a thing, it became important for systems to control what code could be executed on a computer. However, with any new system, programmers are always looking at ways to automate it, and they often create new ways for getting code into the system. Interpreters that allow processing of inputs as code are a common example of this. 172.71.150.63 19:48, 27 September 2022 (UTC)
The current explanation is extremely verbose for such a simple concept, joke, and title text rejoinder. Lots of the discussion is not really on topic. Can we pull some of it out into a "Further considerations" subsection perhaps? 172.69.134.161 02:53, 28 September 2022 (UTC)
- Agree, way to little explanation in too much text. I personally would even delete the whole section on password managers. Think the joke is more related to the web1/2/3 thing, mentioned below, than to password managers. --IamNotJudithPolgar (talk) 19:13, 19 February 2023 (UTC)
The comic is about crypto service companies like crypto.com that are 'one-stop shops for all your decentralisation needs'. The comic refers to both a "two key" system (crypto uses a public and private key encryption) and the title text refers to decentralisation. Bitcoin is designed to be decentralised but it is not convenient to use it in a decentralised fashion. The vast majority of people use centralised services to access it (e.g. crypto.com). These are 'one-stop shops for all your decentralisation needs". I don't have a crypto account with one of these but I'm guessing they might use 2 factor authentication or public / private keys to verify account identity, which only fixes the security problem introduced by the service in the first place.
Kids today with their impatience and demand for instant gratification. Back in my day you actually had to pick up the phone and talk to a human being to initiate a nuclear apocalypse. 172.70.174.159 07:47, 29 September 2022 (UTC)