1934: Phone Security
| Phone Security |
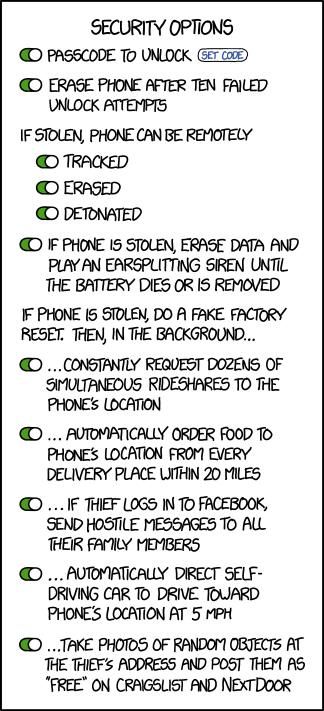 Title text: ...wait until they type in payment information, then use it to order yourself a replacement phone. |
Explanation[edit]
This comic pokes fun at various phone security measures. At first, it covers some real measures, and then continues on to measures that are clearly somewhat overzealous or otherwise humorous. It is worth noting that all of the options are turned ON in the screen shown, so apparently the owner must be very afraid that their phone is going to be stolen, or just wants to see what will happen. These may be options that would appear on the xkcd Phone, but that is not mentioned specifically, and this comic does not appear to be directly linked.
The first two options: Set Passcode to Unlock, and Erase phone after 10 failed unlock attempts are both real security measures found on many phones. The remaining options would rely on the fact that the phone could sense that it is stolen:
If stolen, phone can be remotely... The items on this sub-heading indicate the requirements of a separate device (i.e. the owner's laptop). The phrasing leaves it ambiguous whether they are only available when it is sensed to be stolen, or if they are simply indicators of whether the owner can perform the given actions when activated.
- Tracked: This would allow the police to catch the perpetrator and return your phone. This function is available on most modern phones in general but not bound to a specific situation.
- Erased: This would prevent any sensitive data from being taken by a thief. This function is also available on most modern phones.
- Detonated: This would likely harm the thief, possibly severely, depending on how the phone was detonated. The main problem with this approach (ignoring the possibility of manslaughter), is that if the phone is capable of detonation it's possible, by accident, glitch, or a malicious hacker, that the phone could detonate when not stolen, possibly hurting or killing the rightful owner. It is also possible for the detonation to harm innocent people who happen to be nearby when the feature is triggered. Phone batteries may produce an explosion if their temperature rises high enough, and contain circuitry both inside the battery and inside the logic of the phone to prevent this.
If the phone is stolen, play an earsplitting siren until the battery dies or is removed: This would be to draw attention to the thief, and discourage them from stealing future phones. Noticeably, it does not specify how the phone determines it is stolen, and, similar to the "detonate" option above, this has the potential to be an irritation if it is activated by accident, glitch, or hack.
If the phone is stolen, do a fake factory reset. Then, in the background...: This series of options is all humorous, indicating that the phone would allow the thief to think that it had factory reset, but the phone would, in fact, not do so, and would instead annoy the thief by doing various horrible things to them.
- ...constantly request dozens of simultaneous rideshares to the phone's location: This would cause tons of "rides" to show up at the stolen phone, leaving a lot of annoyed ridesharers, and possibly alerting the police to the thief's location. The thief may begin developing serious paranoia.
- ...automatically order food to the phone's location from every delivery place within 20 miles: This would be similar to the ridesharing issue, except it would be implied that the thief would be on the hook to pay for all of that delivered food. If not, this might arguably be the worst option in this menu, since not only would the owner of the phone have their phone stolen, they would also have hundreds of dollars of delivery bills. This could also lead the police to the thief.
- ...if the thief logs into Facebook, send hostile messages to all their family members: This has now deviated from things that could even possibly be useful, and is now just getting revenge on the thief, or potentially the person that the thief sells the phone to.
- ...automatically direct self driving car to drive toward the phone's location at 5 mph: This would cause a self driving car to follow the thief at a moderate jogging speed, or to run them over when the running ceases. This could absolutely catch the thief, but would also just be really, really creepy.
- ...take photos of random objects at the thief's address and post them as "Free" on Craigslist or NextDoor: Craigslist and NextDoor are sites that allow people to post advertisements for various things. Posting a large number of things for free would cause a lot of people to show up at the thief's residence, which can be found via GPS, requesting the free things, or, more humorously, if the thief was not home, people may just come by and take things, causing them to steal from the thief. This would be a humorous form of poetic justice.
The title text extends the last category with: ...wait until they type in payment information, then use it to order yourself a new phone. If the thief used the thief's own payment information, then this would be the ultimate in poetic justice, as it would basically say that the user does not care if their phone gets stolen, because the thief will end up unintentionally buying them a new one. If the thief were to complain about this, they would have to admit that they had stolen the first phone in order to do so, which they would be disinclined to do. However, if the thief used fraudulent or stolen payment information (whether stolen by the same thief or acquired online), then the replacement phone would be purchased with the payment information of the other victim, and when that person complained, the owner of the stolen phone would appear to be the person who stole the payment information, and might be arrested for that theft. This is a very, very bad idea.[citation needed]
Note that all of these security measures, with the possible exception of the remote detonation, could theoretically be done by a security app on a typical smartphone, although the fake factory reset and most (if not all) of what follows would likely require a phone to be rooted and have a custom operating system installed. With the advent of open source phones such as the Librem 5, tricks such as these have become much easier for the average programmer to implement, and some may already exist in the wild. (Even the remote detonation might be possible on some phones that prevent battery explosions with software rather than physical circuitry.)
Transcript[edit]
- [The content of a configuration screen on a smartphone is shown. All items listed are activated as indicated by green switches.]
- Security Options
- Passcode to unlock (Set Code)
- Erase phone after ten failed unlock attempts
- If stolen, phone can be remotely
- Tracked
- Erased
- Detonated
- If phone is stolen, erase data and play an earsplitting siren until the battery dies or is removed
- If phone is stolen, do a fake factory reset. Then, in the background...
- ...constantly request dozens of simultaneous rideshares to the phone's location
- ...automatically order food to phone's location from every delivery place within 20 miles
- ...if thief logs in to Facebook, send hostile messages to all their family members
- ...automatically direct self-driving car to drive toward phone's location at 5 mph
- ...take photos of random objects at the thief's address and post them as "free" on Craigslist and Nextdoor
Discussion
"Detonated" ah, so this is the feature that Samsung was prototyping last year... Andyd273 (talk) 15:39, 27 December 2017 (UTC)
- Ha! Yes, it's too bad their phones kept mistakenly registering as being stolen... stupid bugs. 172.69.70.107 17:28, 27 December 2017 (UTC) Sam
- Back in the day if a hacker really hated you, you'd come back to your computer and see smoke pouring out of the CPU. I bet there's some way to detonate a phone in software by overheating the battery, but I imagine it could be different for every phone/battery combination. 108.162.219.64 (talk) (please sign your comments with ~~~~)
- Already done. http://www.zdnet.com/article/this-crypto-mining-android-malware-is-so-demanding-it-burst-a-smartphone/ Silverpie (talk) 23:09, 28 December 2017 (UTC)
- I was not here "last year". anybody got links to show me?--me, hi (talk) 19:57, 28 March 2025 (UTC)
- Likely that would be the whole bad battery thing.
- Of course, the comic was published before this other thing happened, so nothing to do with that. 172.70.160.218 21:08, 28 March 2025 (UTC)
Someone needs to make a jailbreak that does as much of this as possible, especially the ridesharing and siren 😂 PotatoGod (talk) 15:52, 27 December 2017 (UTC)
- there was or is at least one house in the U.S. that was reported, apparently inaccurately, as the location of an extraordinary number of stolen cell phones. Presumably that house would suffer all of the pranks that this phone security performs. As for payment details - someone who stole a phone may have also stolen banking cards, so, the account number that you steal back may belong to another innocent victim. It's just a joke of course, but, saying. 162.158.111.235 22:02, 27 December 2017 (UTC)
Made a account just to ask this - why is the post still considered incomplete? It looks complete to me. Donutman (talk) 13:59, 28 December 2017 (UTC)
- Because I added the core explanation, but many improvements have been made since then (bullet points, bolding, transcript). Also, the siren would be insanely easy to do, as would an automated "send the GPS location to the police" among other things. Kashim (talk) 14:15, 28 December 2017 (UTC)
- I've removed the tag right now after I added that the phone would have to sense that it is stolen. There is no sensor to detect this. --Dgbrt (talk) 19:46, 28 December 2017 (UTC)
- Bluetooth. With paired device on owner, the phone can detect if it was moved from owner. -- Hkmaly (talk) 01:19, 29 December 2017 (UTC)
- No good. Firstly, no phone (that I know of) comes with such a device, which I would guess would be called a dongle. Secondly, if they did it wouldn't take long for thieves to realize they have to get the dongle, too. Thirdly, that would mean the owner could never put down their phone, like at home or at work - I've heard of a few workplaces which are high security and don't allow cell phones, so they have to be left in the car or in a locker near the entrance - unless they remember to put down the device too (which would largely defeat the purpose of such a device). And the first time they forget and the phone identified itself as stolen would be enough to convince the rightful owner that this system doesn't work. Fourthly, anything wireless must work by battery. When that battery dies, either the phone would trigger as being stolen, or it would have to detect the battery dying to not go off, in which case you're vulnerable to theft until you charge the ownership dongle. NiceGuy1 (talk) 09:36, 29 December 2017 (UTC)
- All points you raised are real, but don't make it impossible. Sure, it would be bad idea to detonate or something like that when the dongle gets out of range, but it can be used to start making noise (the siren option). For the other countermeasures, the phone should detect being stolen by incorrect password being entered repeatedly. -- Hkmaly (talk) 23:36, 29 December 2017 (UTC)
- Just to follow this up, for most of the countermeasures, it seems relatively clear that the phone would consider itself stolen when somebody tries to wipe it or enters the wrong password too many times. The owner would have some secret wiping procedure that performs a legitimate wipe, and when the phone is wiped using a normal procedure it considers itself stolen and engages all its countermeasures. 108.162.212.107 19:08, 30 December 2017 (UTC)
- All points you raised are real, but don't make it impossible. Sure, it would be bad idea to detonate or something like that when the dongle gets out of range, but it can be used to start making noise (the siren option). For the other countermeasures, the phone should detect being stolen by incorrect password being entered repeatedly. -- Hkmaly (talk) 23:36, 29 December 2017 (UTC)
- No good. Firstly, no phone (that I know of) comes with such a device, which I would guess would be called a dongle. Secondly, if they did it wouldn't take long for thieves to realize they have to get the dongle, too. Thirdly, that would mean the owner could never put down their phone, like at home or at work - I've heard of a few workplaces which are high security and don't allow cell phones, so they have to be left in the car or in a locker near the entrance - unless they remember to put down the device too (which would largely defeat the purpose of such a device). And the first time they forget and the phone identified itself as stolen would be enough to convince the rightful owner that this system doesn't work. Fourthly, anything wireless must work by battery. When that battery dies, either the phone would trigger as being stolen, or it would have to detect the battery dying to not go off, in which case you're vulnerable to theft until you charge the ownership dongle. NiceGuy1 (talk) 09:36, 29 December 2017 (UTC)
- Bluetooth. With paired device on owner, the phone can detect if it was moved from owner. -- Hkmaly (talk) 01:19, 29 December 2017 (UTC)
- I've removed the tag right now after I added that the phone would have to sense that it is stolen. There is no sensor to detect this. --Dgbrt (talk) 19:46, 28 December 2017 (UTC)
- You didn't need an account to write a comment - any commenter name that's an IP address is such a guest commentor. I posted many before I created an account. :) NiceGuy1 (talk) 09:36, 29 December 2017 (UTC)
I first thought "erase phone" meant "erase physically", but "detonate" makes that somewhat redundant. 141.101.105.240 11:54, 29 December 2017 (UTC)
Hahaha!!! Waiting for the iOS update with all these features... Herobrine (talk) 13:45, 18 March 2018 (UTC)
Removed the bit about the 5mph car being similar to the plot of the movie "It Follows". This trope of something stalking someone is too generic to warrant the mention of a specific movie. I commented this on 7 April but forgot to type the wavy thingy. Now, it's 27 July. R3TRI8UTI0N (talk) 03:28, 27 July 2023 (UTC)