Difference between revisions of "2044: Sandboxing Cycle"
m (rv) |
|||
| Line 1: | Line 1: | ||
| − | + | {{comic | |
| + | | number = 2044 | ||
| + | | date = September 10, 2018 | ||
| + | | title = Sandboxing Cycle | ||
| + | | image = sandboxing_cycle.png | ||
| + | | titletext = All I want is a secure system where it's easy to do anything I want. Is that so much to ask? | ||
| + | }} | ||
| + | |||
| + | ==Explanation== | ||
| + | A {{w|Sandpit|sandbox}} or sandpit is a playground where children can play safe without interfering the world outside. By this meaning the term was adopted by others like the {{w|Sand table|sand table}} in military uses, or as a {{w|Wikipedia:Sandbox|Wikipedia Sandbox}}, a playground for inexperienced editors to test their additions, and in {{w|Sandbox (computer security)|computer security (sandbox)}} which [[Randall]] probably references at this comic. | ||
| + | |||
| + | Software is getting more and more complex, and in an effort to reduce programming work and security vulnerabilities, large applications are composed of multiple programs. Getting these mostly self-contained programs to work with each other can be tricky, since requirements can vary a lot between different applications, requiring a rather general {{w|Interface (computing)|interface}} or {{w|API}} for communication. The more open such interfaces are, the higher the risk of unintended side effects, like vulnerabilities and overly permissive data access which could be exploited by hackers. | ||
| + | |||
| + | At the top left panel it could be a software collection whose parts are not yet fully connected to each other; the parts of the system which are as yet unconnected are shown in red, symbolizing a problem. A simple example is a typical {{w|Productivity_software#Office_suite|office suite}} used for documents, presentations, spreadsheets, charts, databases, and more. In the early days those separate applications weren't much connected together, copy and paste was one of the most important features; which suggests the applications haven't yet been fully developed. However, software is never fully developed, improvements can always be made. | ||
| + | |||
| + | The next panel uses some "new technology" (in green, representing a solution) to interconnect those parts not only internal but also to the world outside at the internet. In the simple office suite example this means a document can now use a spreadsheet directly by using just a simple connection to another file. If that spreadsheet is changed the document uses this new content without any need of copying it manually. | ||
| + | |||
| + | But this leads to the third panel, with undesired connections shown in red. The undesired connections mean that problems in specific applications may spread to other applications because nobody can oversee everything in a large environment. It even may destroy the original document in the office suite example or allow malicious users to exploit security holes. | ||
| + | |||
| + | The fourth panel shows (in green, representing a solution) a method applied to this problem known as sandboxing. This is a security mechanism for separating running programs without risking harm to others. This can tighten up sloppy security. A direct consequence of restricted communication is that the programs now again can't connect easily to each other, resulting in a situation very similar like in the first panel and restarting the "sandboxing cycle." | ||
| + | |||
| + | The point made by this comic is that it is often difficult to easily use a system without lowering security in that system; a dilemma that can be found both in the office suite example above or the social media example below. | ||
| + | |||
| + | The dilemma is again stated in the title text: Randall wants both ease of use and high security. In practice, a tradeoff has to be made. | ||
| + | |||
| + | ==Transcript== | ||
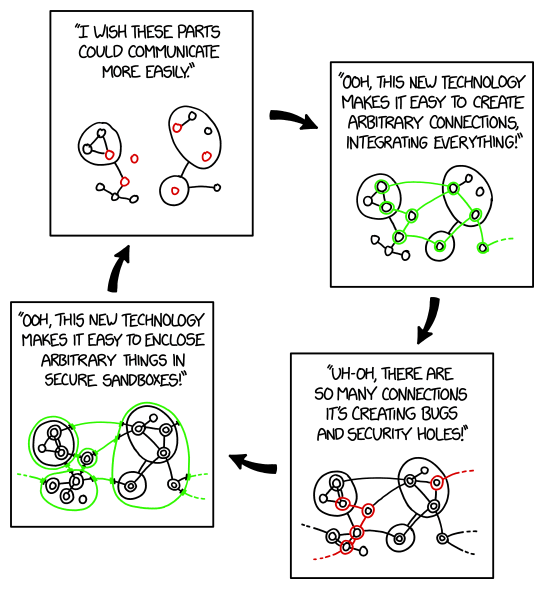
| + | :[The comic consists of four panels arranged in a circle around the center. Black arrows connecting them clockwise in an infinite loop. All panels show the same 14 tiny circles and three different rings embedding some of the circles while other circles are outside. A few circles and rings are connected by lines but there is no connection between them all.] | ||
| + | |||
| + | :[The panel at top left shows this configuration but with a few circles in red.] | ||
| + | :"I wish these parts could communicate more easily." | ||
| + | |||
| + | :[Clockwise the next panel on the right shows new lines in green connecting nearly all remaining also now green circles and the lower most circle has a dashed green line to the outside.] | ||
| + | :"Ohh, this new technology makes it easy to create arbitrary connections, integrating everything!" | ||
| + | |||
| + | :[At the third panel to the bottom right all green parts are now in black and even more connections are established. Parts of these and some others are now highlighted in red.] | ||
| + | :"Uh-oh, there are so many connections it's creating bugs and security holes!" | ||
| + | |||
| + | :[At the fourth panel to the bottom left all red parts are now in black, showing a complex structure. Four green rings separate the structure with only green connections between them and to the outside.] | ||
| + | :"Ohh, this new technology makes it easy to enclose arbitrary things in secure sandboxes!" | ||
| + | |||
| + | :[The arrow above the fourth panel connects it to the first and the circle continues from the beginning.] | ||
| + | |||
| + | ==Trivia== | ||
| + | *While this comic is applicable to a wide number of digital security issues, it may be about social media in particular. | ||
| + | |||
| + | *Originally, there were only a few social media websites (AOL, for example), which were not connected to one another but were so large and all-encompassing that they could be considered highly-connected systems. Once the internet became more popular and more powerful, lots of smaller websites popped up for individual topics -- forums, web apps, etc. Eventually there were so many places users had to log in that Google and Facebook began to offer services to use a single log-in for all websites that opted-in to supporting that service. Recently, with increasing consumer concerns about privacy and security, some users have begun to deliberately sever the connections between websites, to make it harder for any one company to gain a monopoly on their data. This may not last long, though, as users realized just how inconvenient it is to manage so many logins. | ||
| + | |||
| + | *This desire to accommodate both privacy and ease use of use can lead to confusing and paradoxical actions or outlooks, like [[2045|Randall's struggle with his social media accounts in the comic immediately following this one]], or Zach Wienersmith's complaints in the [https://www.smbc-comics.com/comic/the-problem SMBC comic] released the same day as this one. | ||
| + | |||
| + | {{comic discussion}} | ||
| + | |||
| + | [[Category:Comics with color]] | ||
| + | [[Category:Charts]] | ||
| + | [[Category:Computer security]] | ||
Revision as of 23:32, 4 May 2022
| Sandboxing Cycle |
 Title text: All I want is a secure system where it's easy to do anything I want. Is that so much to ask? |
Explanation
A sandbox or sandpit is a playground where children can play safe without interfering the world outside. By this meaning the term was adopted by others like the sand table in military uses, or as a Wikipedia Sandbox, a playground for inexperienced editors to test their additions, and in computer security (sandbox) which Randall probably references at this comic.
Software is getting more and more complex, and in an effort to reduce programming work and security vulnerabilities, large applications are composed of multiple programs. Getting these mostly self-contained programs to work with each other can be tricky, since requirements can vary a lot between different applications, requiring a rather general interface or API for communication. The more open such interfaces are, the higher the risk of unintended side effects, like vulnerabilities and overly permissive data access which could be exploited by hackers.
At the top left panel it could be a software collection whose parts are not yet fully connected to each other; the parts of the system which are as yet unconnected are shown in red, symbolizing a problem. A simple example is a typical office suite used for documents, presentations, spreadsheets, charts, databases, and more. In the early days those separate applications weren't much connected together, copy and paste was one of the most important features; which suggests the applications haven't yet been fully developed. However, software is never fully developed, improvements can always be made.
The next panel uses some "new technology" (in green, representing a solution) to interconnect those parts not only internal but also to the world outside at the internet. In the simple office suite example this means a document can now use a spreadsheet directly by using just a simple connection to another file. If that spreadsheet is changed the document uses this new content without any need of copying it manually.
But this leads to the third panel, with undesired connections shown in red. The undesired connections mean that problems in specific applications may spread to other applications because nobody can oversee everything in a large environment. It even may destroy the original document in the office suite example or allow malicious users to exploit security holes.
The fourth panel shows (in green, representing a solution) a method applied to this problem known as sandboxing. This is a security mechanism for separating running programs without risking harm to others. This can tighten up sloppy security. A direct consequence of restricted communication is that the programs now again can't connect easily to each other, resulting in a situation very similar like in the first panel and restarting the "sandboxing cycle."
The point made by this comic is that it is often difficult to easily use a system without lowering security in that system; a dilemma that can be found both in the office suite example above or the social media example below.
The dilemma is again stated in the title text: Randall wants both ease of use and high security. In practice, a tradeoff has to be made.
Transcript
- [The comic consists of four panels arranged in a circle around the center. Black arrows connecting them clockwise in an infinite loop. All panels show the same 14 tiny circles and three different rings embedding some of the circles while other circles are outside. A few circles and rings are connected by lines but there is no connection between them all.]
- [The panel at top left shows this configuration but with a few circles in red.]
- "I wish these parts could communicate more easily."
- [Clockwise the next panel on the right shows new lines in green connecting nearly all remaining also now green circles and the lower most circle has a dashed green line to the outside.]
- "Ohh, this new technology makes it easy to create arbitrary connections, integrating everything!"
- [At the third panel to the bottom right all green parts are now in black and even more connections are established. Parts of these and some others are now highlighted in red.]
- "Uh-oh, there are so many connections it's creating bugs and security holes!"
- [At the fourth panel to the bottom left all red parts are now in black, showing a complex structure. Four green rings separate the structure with only green connections between them and to the outside.]
- "Ohh, this new technology makes it easy to enclose arbitrary things in secure sandboxes!"
- [The arrow above the fourth panel connects it to the first and the circle continues from the beginning.]
Trivia
- While this comic is applicable to a wide number of digital security issues, it may be about social media in particular.
- Originally, there were only a few social media websites (AOL, for example), which were not connected to one another but were so large and all-encompassing that they could be considered highly-connected systems. Once the internet became more popular and more powerful, lots of smaller websites popped up for individual topics -- forums, web apps, etc. Eventually there were so many places users had to log in that Google and Facebook began to offer services to use a single log-in for all websites that opted-in to supporting that service. Recently, with increasing consumer concerns about privacy and security, some users have begun to deliberately sever the connections between websites, to make it harder for any one company to gain a monopoly on their data. This may not last long, though, as users realized just how inconvenient it is to manage so many logins.
- This desire to accommodate both privacy and ease use of use can lead to confusing and paradoxical actions or outlooks, like Randall's struggle with his social media accounts in the comic immediately following this one, or Zach Wienersmith's complaints in the SMBC comic released the same day as this one.
Discussion
It’s not just sand boxing that follows this kind of cycle, other design ideas follow similar iterations from generation to generation. The grass is always greener... 172.68.34.94 04:55, 10 September 2018 (UTC)
Interesting that the same red and green colours have been used for two comics in a row. Baquea (talk) 05:18, 10 September 2018 (UTC)
This seems linked to the British Airways (BA) Data breach. https://www.bbc.co.uk/news/uk-england-london-45440850 From the precise time frame it is likely that was how long a piece of code (the one with the "link going nowhere") was in use. RIIW - Ponder it (talk) 17:41, 10 September 2018 (UTC)
The one thing that we learn from history is that nobody ever learns anything from history..... Gearóid (talk) 05:56, 10 September 2018 (UTC)
I've started explaining this comic, but it is far from done. We should probably address some of the undertones (history repeating itself, software getting more and more complex to do the same thing it did before, the constant cycle of improvement we expect from software products,...) //gir.st/ (talk) 10:42, 10 September 2018 (UTC)
It's not only software
Right now I see two other things also matching the graph: The internet vs. firewalling, and the imposition of duties by the US against free-trade with China and Europe. An because the comic doesn't mention software anyway I think the explanation should be more universal at the first place. It's the more common problem between being open and secure. Software is just one example. --Dgbrt (talk) 13:04, 10 September 2018 (UTC)
- While my two examples before matched the graph they don't fit to the comic at all. A sandbox is primarily a box where everyone inside can do anything without effecting others outside. And while this comic is probably about software - only small hints like bug and security are given - a sandbox is still a playing ground (not only for children.) --Dgbrt (talk) 19:23, 10 September 2018 (UTC)
SMBC is so similar sometimes... Even down to using the phrase "is that too much to ask"!
Does anyone else here read smbc-comics? Today's: http://www.smbc-comics.com/comic/the-problem
All I want is a webcomic that is timely, topical, & mirrors my own sentiments on a day-to-day basis without feeling redundant or eerily informed. Is that too much to ask? ProphetZarquon (talk) 15:38, 10 September 2018 (UTC)
- I don't see social media as mentioned at SMBC as the major part in this comic, but the same phrase "is that too much to ask" is probably more than just a coincidence. --Dgbrt (talk) 19:02, 10 September 2018 (UTC)
Gotta say, that map of the nodes looks vaguely "US shaped", I'd guess that this is especially referencing connecting various datacenters? R167 (talk) 16:11, 10 September 2018 (UTC)
re:Transcript:
sorry for botching the transcript and i appreciate you fixing my mistake (i'll learn, i promise). i do think though that my version was contentwise better: i tried to make it as concise as possible and explaining 'why' instead of exactly how it is pictured.
i believe we shouldn't describe minute details (e.g. '14 nodes', 'clockwise', ...) and do include what is meant to be depicted ('likely indicating bugs') as in the faq states: someone should understand the comic if it was being read to them. i'm keeping it as-is for now, with the hope that we can find some middle ground down the line ;-) //gir.st/ (talk) 19:39, 10 September 2018 (UTC)
- Many thanks for your first draft. But: A transcript describes what can be seen, exactly that but not more. Everything else belongs the the explanation on top. And I wouldn't count 114 nodes but 14 is more than a few but less than hundreds. And the clockwise orientation is really important - think about impaired (blind) people. BTW: Please avoid html-tags here. --Dgbrt (talk) 20:14, 10 September 2018 (UTC)
The focus on a single application's parts / developpment doesn't make much sense here. Network (with various machines / applications communicating with each other) is a much more likely explanation. 108.162.229.100 (talk) (please sign your comments with ~~~~)
I have a question. Do the big green circles in the bottom-left represent the tiny red circles in the top left, and thus the cycle moves "up" a level with each iteration? Or is it all on the same level and the sandboxing divides are drawn and redrawn in every cycle? 172.68.133.168 16:02, 12 September 2018 (UTC)
- The infinite loop only does work when the tiny circles always represent the same entity. It's drawn by hand but they are in each frame at the same relative position. Nevertheless the colors should be explained. --Dgbrt (talk) 16:52, 12 September 2018 (UTC)
Can someone explain the colors? Herobrine (talk) 13:12, 13 September 2018 (UTC)
- My explanation, green is things doing good/what he wants them to, red is not doing what he wants or making connections he wants. Not sure where to put it in the explanation - Welp 172.68.46.41 17:29, 2 October 2018 (UTC)
- I explained the colors in the explanation just now; as such, shall the incomplete tag be deleted? 162.158.106.168 23:29, 24 October 2018 (UTC)
