Difference between revisions of "2030: Voting Software"
(→Transcript: add more to transcript; multiple cueballs) |
(→Blockchain: Looks like it was missing a conjunction (maybe just a "/", but realistically could be one, the other or (very intentionally) both).) |
||
| (12 intermediate revisions by 10 users not shown) | |||
| Line 8: | Line 8: | ||
==Explanation== | ==Explanation== | ||
| − | + | This comic is a commentary on voting machines specifically, and more generally the contrast between what experts will trust and what the average user will trust. | |
| − | The comic | + | The first two panels of this comic involve a reporter talking to professional mechanical engineers, asking about the given safety of the products/solutions that each of their fields help to produce (airplanes from aircraft designers in panel 1, elevators from building engineers in panel 2). While the two inventions selected are relatively new when compared to how long humans have existed, the two fields mentioned have existed for multiple human generations, giving enough time to find flaws in their products/solutions and solve said flaws to the point that they can be considered safe for the general public to use. |
| − | + | The comic from panel 3 onwards contrasts this with computer engineers [[Megan]] and [[Cueball]], both agreeing that their given field (computer science/software development/software engineering) does not have the overall consistent competency that other fields have (or at least appear to have). Indeed, at least anecdotally there are very few ethical and security restrictions for what developers can/cannot do, and relatively minor consequences when catastrophes arise from poor decisions. | |
| − | + | When the reporter follows the interview up with a mention of {{w|blockchain}} technology, Megan and Cueball reflexively tell the reporter to avoid any voting system using the technology at all costs. {{w|Blockchain}} is a relatively new technology that is intended to solve some computer security issues by making it difficult to doctor old data. However, in the process of solving the old computer security issues, it has introduced new computer security issues that have not yet been ironed out; for instance, it doesn't solve input fraud issues, only data-doctoring fraud, so if a program caused the voting machine to record a vote for candidate B whenever a vote for candidate A was cast (such a program could be uploaded to the voting machines through USB, or through the internet which the voting machine must be connected to for blockchain), blockchain would not prevent it. Blockchain has also had a large number of high-profile scams, thefts, and implementations with critical security holes. Thus, [[Megan]] and [[Cueball]] may not trust this blockchain solution because of this history. | |
| − | + | The title text confirms the comic's stance by implicitly saying that any digital voting systems are to not be used under ''any'' circumstances. It may also highlight that anyone working in the field is vulnerable to corruption, or at least that the field is far from maturity. Humorously the title text says digital voting systems should still be ''developed,'' but mostly to keep the people who want to use them occupied, rather than allowing them to actually publish their work in the real world where it can cause serious harm. | |
| − | This fear of computerized voting is a result of a fundamental difference between computer security and other types of safety measures | + | Computer systems, operating primarily in a digital domain, fail differently from most traditional areas of engineering, which operate in analog (or continuous) domains. A small error in an analog part often gives a result which is close to the desired properties (it almost fits, it works most of the time). By contrast, a small error in a digital system (just one bit being changed) can easily make the system function in radically different ways (if not just crash entirely). So not only is software engineering younger than other areas of engineering, but the domain is much less forgiving. Even small errors/variations produce catastrophe down the line. |
| + | |||
| + | This fear of computerized voting is a result of a fundamental difference between computer security and other types of safety measures: Most engineers only have to deal with wear and tear, and very rarely have to guard against sabotage. In contrast, in cryptography there is ''always'' somebody trying to undo what you've built. Not only that, but new advances in cryptography tend to point out vulnerabilities with previous versions, making them not only obsolete, but dangerously so. For these reasons, it is especially important to make sure that whoever is selling you the security method is both competent and non-malicious, but because crypto software is highly technical and often confidential/proprietary, it can be hard to verify this if you're not an expert in the field (which you won't be, if you're buying it). | ||
These issues are especially pertinent to {{w|voting machine}}s, which store incredibly sensitive information but are often catastrophically outdated due to lack of funding. There are also major issues with electronic voting in general; for example, [https://www.youtube.com/watch?v=w3_0x6oaDmI this video from Computerphile] raises issues of malware infections, transferring the votes to the election authorities without having them intercepted, and needing to trust both the machine's software and central counting system to present an accurate account of the votes. Furthermore, the people purchasing them, the politicians, are generally not known for their technical understanding -- or their impartiality. | These issues are especially pertinent to {{w|voting machine}}s, which store incredibly sensitive information but are often catastrophically outdated due to lack of funding. There are also major issues with electronic voting in general; for example, [https://www.youtube.com/watch?v=w3_0x6oaDmI this video from Computerphile] raises issues of malware infections, transferring the votes to the election authorities without having them intercepted, and needing to trust both the machine's software and central counting system to present an accurate account of the votes. Furthermore, the people purchasing them, the politicians, are generally not known for their technical understanding -- or their impartiality. | ||
| − | + | Interestingly, this comic was posted a day before DEF CON 2018, and it was shown there that the voting systems that will be used across America for the mid-term vote in November are, in many cases, extremely insecure. The topic of voting machines has been covered before in [[463: Voting Machines]], where the use of anti-virus software on the machines has been discussed. | |
| − | + | ===Blockchain=== | |
| + | The way blockchain works is that several computers have data being inputted into them. With each tick, they all share their current states with each other, and encrypt and hash it. That state then becomes a 'block' in the chain. They then share states, including that block as part of the state, then hash and encrypt it, and then it becomes a 'block' in the chain. Each 'block' is included in the cryptographic hash of all following blocks, so if a change is made to any given block, all blocks after that block must be changed. | ||
| − | + | Due to the distributed nature, if changes are made to any chain, it can be compared against the other chains, and so long as the majority say that the changes didn't happen, it's reverted and removed. | |
| − | + | This is really great at preventing post-facto data changes. With blockchain you can somewhat guarantee that no one comes in after the election and changes the votes on the machines. (Unless they're handling the blockchain in a stupid fashion, for example without the distribution.) What you cannot do is prevent someone from installing a program on the machine that makes it think that there's a voter when it's idle, and makes it start registering the correct sequence of actions to signify a vote while idle. | |
| − | + | Also, the security issues that Blockchain solves could also be solved via write-once memory, which would be more secure and more difficult to doctor. | |
| − | |||
| − | |||
| − | + | Most computer security specialists are more worried about programs that randomly and/or deliberately misreport a vote, than people changing the votes after they're already recorded, so blockchain would solve an issue that most computer security specialists are less worried about, while causing new issues (the perpetual internet connection among them). | |
==Transcript== | ==Transcript== | ||
| Line 77: | Line 78: | ||
[[Category:Comics featuring Hairy]] | [[Category:Comics featuring Hairy]] | ||
[[Category:Comics featuring Ponytail]] | [[Category:Comics featuring Ponytail]] | ||
| + | [[Category:Aviation]] | ||
[[Category:Elections]] | [[Category:Elections]] | ||
[[Category:Programming]] | [[Category:Programming]] | ||
Latest revision as of 00:36, 27 March 2024
Explanation[edit]
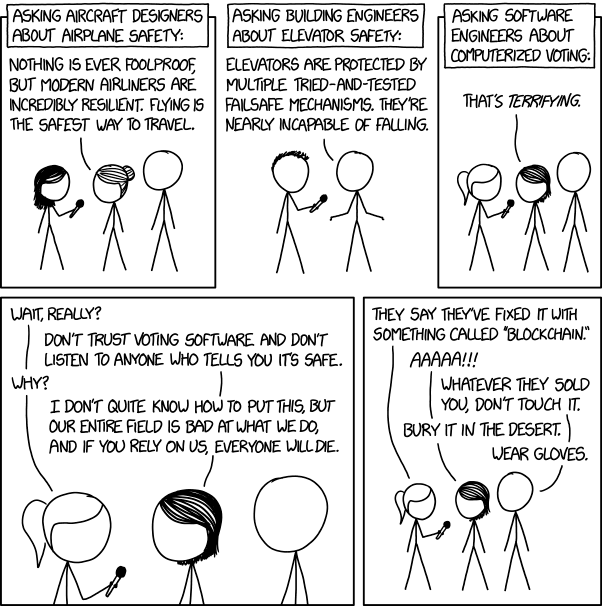
This comic is a commentary on voting machines specifically, and more generally the contrast between what experts will trust and what the average user will trust.
The first two panels of this comic involve a reporter talking to professional mechanical engineers, asking about the given safety of the products/solutions that each of their fields help to produce (airplanes from aircraft designers in panel 1, elevators from building engineers in panel 2). While the two inventions selected are relatively new when compared to how long humans have existed, the two fields mentioned have existed for multiple human generations, giving enough time to find flaws in their products/solutions and solve said flaws to the point that they can be considered safe for the general public to use.
The comic from panel 3 onwards contrasts this with computer engineers Megan and Cueball, both agreeing that their given field (computer science/software development/software engineering) does not have the overall consistent competency that other fields have (or at least appear to have). Indeed, at least anecdotally there are very few ethical and security restrictions for what developers can/cannot do, and relatively minor consequences when catastrophes arise from poor decisions.
When the reporter follows the interview up with a mention of blockchain technology, Megan and Cueball reflexively tell the reporter to avoid any voting system using the technology at all costs. Blockchain is a relatively new technology that is intended to solve some computer security issues by making it difficult to doctor old data. However, in the process of solving the old computer security issues, it has introduced new computer security issues that have not yet been ironed out; for instance, it doesn't solve input fraud issues, only data-doctoring fraud, so if a program caused the voting machine to record a vote for candidate B whenever a vote for candidate A was cast (such a program could be uploaded to the voting machines through USB, or through the internet which the voting machine must be connected to for blockchain), blockchain would not prevent it. Blockchain has also had a large number of high-profile scams, thefts, and implementations with critical security holes. Thus, Megan and Cueball may not trust this blockchain solution because of this history.
The title text confirms the comic's stance by implicitly saying that any digital voting systems are to not be used under any circumstances. It may also highlight that anyone working in the field is vulnerable to corruption, or at least that the field is far from maturity. Humorously the title text says digital voting systems should still be developed, but mostly to keep the people who want to use them occupied, rather than allowing them to actually publish their work in the real world where it can cause serious harm.
Computer systems, operating primarily in a digital domain, fail differently from most traditional areas of engineering, which operate in analog (or continuous) domains. A small error in an analog part often gives a result which is close to the desired properties (it almost fits, it works most of the time). By contrast, a small error in a digital system (just one bit being changed) can easily make the system function in radically different ways (if not just crash entirely). So not only is software engineering younger than other areas of engineering, but the domain is much less forgiving. Even small errors/variations produce catastrophe down the line.
This fear of computerized voting is a result of a fundamental difference between computer security and other types of safety measures: Most engineers only have to deal with wear and tear, and very rarely have to guard against sabotage. In contrast, in cryptography there is always somebody trying to undo what you've built. Not only that, but new advances in cryptography tend to point out vulnerabilities with previous versions, making them not only obsolete, but dangerously so. For these reasons, it is especially important to make sure that whoever is selling you the security method is both competent and non-malicious, but because crypto software is highly technical and often confidential/proprietary, it can be hard to verify this if you're not an expert in the field (which you won't be, if you're buying it).
These issues are especially pertinent to voting machines, which store incredibly sensitive information but are often catastrophically outdated due to lack of funding. There are also major issues with electronic voting in general; for example, this video from Computerphile raises issues of malware infections, transferring the votes to the election authorities without having them intercepted, and needing to trust both the machine's software and central counting system to present an accurate account of the votes. Furthermore, the people purchasing them, the politicians, are generally not known for their technical understanding -- or their impartiality.
Interestingly, this comic was posted a day before DEF CON 2018, and it was shown there that the voting systems that will be used across America for the mid-term vote in November are, in many cases, extremely insecure. The topic of voting machines has been covered before in 463: Voting Machines, where the use of anti-virus software on the machines has been discussed.
Blockchain[edit]
The way blockchain works is that several computers have data being inputted into them. With each tick, they all share their current states with each other, and encrypt and hash it. That state then becomes a 'block' in the chain. They then share states, including that block as part of the state, then hash and encrypt it, and then it becomes a 'block' in the chain. Each 'block' is included in the cryptographic hash of all following blocks, so if a change is made to any given block, all blocks after that block must be changed.
Due to the distributed nature, if changes are made to any chain, it can be compared against the other chains, and so long as the majority say that the changes didn't happen, it's reverted and removed.
This is really great at preventing post-facto data changes. With blockchain you can somewhat guarantee that no one comes in after the election and changes the votes on the machines. (Unless they're handling the blockchain in a stupid fashion, for example without the distribution.) What you cannot do is prevent someone from installing a program on the machine that makes it think that there's a voter when it's idle, and makes it start registering the correct sequence of actions to signify a vote while idle.
Also, the security issues that Blockchain solves could also be solved via write-once memory, which would be more secure and more difficult to doctor.
Most computer security specialists are more worried about programs that randomly and/or deliberately misreport a vote, than people changing the votes after they're already recorded, so blockchain would solve an issue that most computer security specialists are less worried about, while causing new issues (the perpetual internet connection among them).
Transcript[edit]
- [A Megan-like woman, with bushy hair, is holding a handheld microphone and interviewing Hairbun and Cueball, standing in a line]
- [Heading above the panel]:
- Asking aircraft designers about airplane safety:
- Hairbun: Nothing is ever foolproof, but modern airliners are incredibly resilient. Flying is the safest way to travel.
- [In a frameless panel, Hairy is holding a handheld microphone and interviewing Cueball]
- [Heading above the panel]:
- Asking building engineers about elevator safety:
- Cueball: Elevators are protected by multiple tried-and-tested failsafe mechanisms. They're nearly incapable of falling.
- [Ponytail is holding a handheld microphone and interviewing Megan and Cueball, standing in a line]
- [Heading above the panel]:
- Asking software engineers about computerized voting:
- Megan: That's terrifying.
- [Zoomed in on Ponytail, Megan and Cueball's faces]
- Ponytail: Wait, really?
- Megan: Don't trust voting software and don't listen to anyone who tells you it's safe.
- Ponytail: Why?
- Megan: I don't quite know how to put this, but our entire field is bad at what we do, and if you rely on us, everyone will die.
- [Zoomed back out, showing Ponytail, Megan and Cueball standing in a line]
- Ponytail: They say they've fixed it with something called "blockchain."
- Megan: AAAAA!!!
- Cueball: Whatever they sold you, don't touch it.
- Megan: Bury it in the desert.
- Cueball: Wear gloves.
Discussion
This comic is eerily relevant again these days! 172.69.190.72 14:22, 22 November 2020 (UTC)
Well the 'airplanes' part of this comic has aged really damn poorly :(
- I mean, from what I've heard the problems are more with quality control at Boeing than the engineering itself Stardragon (talk) 00:32, 27 March 2024 (UTC)
I think this comic is referencing this twitter thread and the controversy behind it. 172.69.190.4 17:59, 8 August 2018 (UTC)
- The Experts criticize West Virginia’s plan for smartphone voting article on ArsTechnica has more information (as much as possible when the company in question does not provide any details (note that it is about overseas voting). --JakubNarebski (talk) 19:44, 8 August 2018 (UTC)
Is he saying it's weird that we're so sophisticated in other areas of computer science but so far behind in voting technology, or is he making fun of the idea that electronic voting is somehow inherently unsafe?--108.162.216.106 18:10, 8 August 2018 (UTC)
- No i think he is saying computer science is a mess and we should not trust it with voting(he is not making fun of the idea of it being unsafe, he is pressing on the point of it being unsafe[saying that all experts agree on that])18:18, 8 August 2018 (UTC)
- I think he's commenting on how in most fields, the experts are very sure that they do their job well, and all the angles have been tried and tested, but in computer science the experts are more certain than anyone that there is absolutely no way for a person to actually build a complex software system with no flaws or vulnerabilities, even if they controlled every aspect of the system. in practice of course they control very little of the system and understand even less of it. 172.68.34.88 18:22, 8 August 2018 (UTC)
- He's saying that software development is a terribly buggy process, most likely because the majority of software out there can have bugs without very dire real-world consequences (unlike aircraft or elevators).
- Not to mention the fact that there are incredibly smart people with great interest in undoing the work that software developers do, whereas that isn't at all the case with airplanes or elevators. 108.162.219.214 18:29, 8 August 2018 (UTC)
- Plus there's the general issue that the public as a whole takes the view that "Computers are majykal" (misspelling deliberate) and therefore somehow automatically safe & infallible, despite experts trying very hard to disillusion people about...pretty much all of that. Compare that to the common assumptions about aircraft and elevators--people need the safety verified, instead of assuming it like they do with computers. Werhdnt (talk) 19:08, 8 August 2018 (UTC)
- There's a logical fallacy here. To compare airplaneS and elevatorS to a voting system program is comparing plural to singular. There would be significant opportunity to break/modify a single instance of those objects, although without the relative anonymity of electronic access involved. Once a computer system is infiltrated, the break-in can be replicated to all instances of that program relatively instantaneously, assuming communication pathways are available.162.158.75.130 19:12, 8 August 2018 (UTC)
- No logical fallacy; there have been multiple attempts to get people to accept a voting system program, and the 'done by a computer=infallible' problem is not unique to voting programs. Mr. Babbage was being confused by people who were thinking it was possible to get the correct answers from a computer despite putting the wrong data in back in the 1860s (at least!), and the computer at the time was not much more than a fancy calculator. Werhdnt (talk) 20:23, 8 August 2018 (UTC)
A blockchain node doesn't technically need to be connected to the internet in order to function. It needs to have some method for receiving messages from other nodes on the blockchain network, and most blockchain nodes do indeed get these messages via the internet, but some magic beans nodes (for example) get updates about new blocks and new transactions from the Blockstream satellite. An internet connection is therefore not intrinsically necessary for a blockchain to work, it's just the most convenient way to do it.
- The blockstream satellite is an internet, just a different media. 172.68.59.24 14:41, 11 August 2018 (UTC)
Do you think that this comic had anything to do with the debacle in Johnson County, KS last night? 162.158.62.231 19:30, 8 August 2018 (UTC)
The comic ignores the fact that modern airplanes are heavily utilizing software of all kinds. A software failure in an aircraft could easily be fatal (and have been so various times in history already, while the consequences of a voting software working incorrect are relatively harmless), and still airplanes remain safe, as the comic recognizes. --YMS (talk) 21:05, 8 August 2018 (UTC)
- Airplanes are not connected to internet and reasonably well protected from people putting their USB devices in their control system. Also, they are NOT build by lowest bid contractor. There ARE people now capable of building offline voting machine which would be reasonable secure. They are working in banks and stock exchanges and at those companies providing switches for internet backbone, are extremely well paid and wouldn't ever promise they will get the machine finished in single year. Noone asks THEM to make the voting machines. Voting over internet? With consumer-grade devices? Impossible. (I'm also working in IT, although not on mentioned high-security systems.) -- Hkmaly (talk) 22:24, 8 August 2018 (UTC)
- Note that she is talking to aircraft designers, not to software engineers working on fly-by-wire systems (back when I took software engineering you got an answer similar to the one about voting machines when discussing fly-by-wire). I took this more as the aircraft designers glossing over the problems caused by software engineering. A voting system which uses paper ballots, with perhaps computer systems used for some stages of counting would be a reasonable analogy to the redundant systems used in aircraft. 162.158.106.228 23:08, 8 August 2018 (UTC)
Seems to me that the last panel references the E.T for Atari Desert Burial (https://en.wikipedia.org/wiki/Atari_video_game_burial), perhaps to draw some analogy as to the potential quality or likelihood of success of a Block-chain solution as compared to the ill-fated video game. Anyone think that's worth explaining? Da_NKP 10:15, 8 August 2018 (UTC) Da_NKP
What motive is there to "mine DemocracyCoin"? Who evaluates this blockchain? 162.158.150.100 22:27, 8 August 2018 (UTC)
- That's simple, ideally it would be a private blockchain, and the evaluators would just be every voting computer in existence (They'd all be active for a similar fairly short time period). Presumably the evaluations would be ongoing during the voting process, then could be stopped once voting was complete. The last few votes of the night may not wind up being evaluated. 162.158.74.225
- "The last few votes of the night may not wind up being evaluated" Thats horrifying. That alone should prove how terrible of an idea this is. 162.158.154.181 17:14, 9 August 2018 (UTC)
Wouldn't it be possible to run said blockchain on one's personal computer, instead of running on a voting machine? and you could compile open source software yourself to perform the voting. That sounds like a solid enough way to keep security fine to me, but if I'm missing something, please tell me. TheSandromatic (talk) 03:25, 9 August 2018 (UTC)
- The bigger challenge in a voting system isn't making sure someone doesn't modify the record, it's making sure that each person only votes once and only for themselves -- think about past internet voting campaigns: Justin Bieber wasn't sent to North Korea by *changed* votes, but rather by flooding the system with *bogus* votes. 172.68.132.47 06:26, 9 August 2018 (UTC)
- To be a bit clearer, magic beans (for example), doesn't and can't enforce that wallets correspond one-to-one with people -- multiple people can share a wallet (if they all know the private key), and one person can have multiple wallets. If you want to guarantee one-to-one correspondence, you have to validate identities and issue unique, signed keys at some prior point. Leaving aside whether or not it's possible to do this part securely and without error (and how big of a target the root signing key would be), you then have millions of people doing their own key management, just like you do with magic beans. When magic beans wallets are stolen en masse by key compromises (which does happen), only the wallet owners (who were ostensibly using poor security practices which allowed the compromise) suffer, so the harm is limited. If voting system keys were stolen en masse, but the votes still counted, society as a whole would likely suffer. 172.68.132.47 07:03, 9 August 2018 (UTC)
I think a problem that lies within voting machines is that a single flaw can and will be exploited along all machines. You wouldn't enter a plane if one plane crashing means that all other planes will crash too.
I am not American and not so inside American politics and its system, but I think there right now is (or just was) some kind of vote in Ohio? Randalls other comic about voting machines, (463)references Ohio directly as well. Even if not, that comic should definitely be referenced here. If no one else does I will in a few hours when I come home from work. Lupo (talk) 08:11, 9 August 2018 (UTC)
- There was a special election for Ohio's 12th Congressional District on Tuesday to fill in a vacant spot in the US House of Representatives, yes. I hadn't heard anything specifically about any issues with Ohio's voting machines, though I do somewhat vaguely remember Randall making a comic that expressed horror at the fact that a voting machine needed anti-virus software in the first place. 162.158.63.154 12:58, 9 August 2018 (UTC)
I guess this may be of interest for reasons why not to have electroni voting https://www.youtube.com/watch?v=w3_0x6oaDmI 162.158.154.13
Wait, so I'm not into this *at all*, but a bunch of you seem to be, so:
paper ballot voting works because we can assume the humans we choose to count oue votes to be trustworthy. Imagine that as the digital voting device, we use a cheapo Chinaphone. We remove any parts needed for wireless connection, and all USB ports and AUX ports (which are the only ports on such a device) are filled with hot glue (so, destroyed). Some of them are designed in an awkward way where you have to take the backside off in order to access the SD card, which normally is disadvantageous, but now it means that you can use a sort of sturdy phone cover with a physical lock to make the SD card inaccessible to anyone not owning the key. The key is with the trustworthy human that would otherwise hold the key for the box the paper votes go in. You could glue or screw the charger to it, so it was always full and you couldn't put a USB stick into that port without breaking the actual thing - and the trustworthy voting office humans would notice that. If it saves all votes on some SD card, the humans we trust to work for the voting can take the SD cards out, and bring them to a central computer that also has no wireless parts, and some trustworthy humans watching the SD ports. That central computer saves all the votes and counts them.
If you doctor with paper votes, then you'd have to destroy them or there'd be evidence against you. Destroying them is not safe to do.
If something seems fishy, then paper votes can be recounted.
If you have a voting machine that only a trustworthy person has access to, then that means that this trustworthy person has to build every part of the machine from the smallest transistor on and also has to guard the machine the whole time. Because otherwise you could manipulate the machine in a way to count the votes wrong, but show correct results when you test it. Since this is completely unpractical in the end you'd have to count by hand anyway.162.158.91.251 12:53, 10 August 2018 (UTC)
- Or just use paper ballots. They have been a perfectly adequate solution for centuries, and will continue to do so forever (and no, the paper usage for voting is not really significant, compared to the paper usage overall). 162.158.202.64 20:00, 10 August 2018 (UTC)
If also we delete any and all software and firmware on the phones and central computer, and replace it by a piece of software that can literally only show you a multiple choice screen with names of candidates and save what you clicked, that sounds quite safe. Carrying the SD cards to the central computer would still take time, but we're carrying much smaller things so it might speed up somewhat (less stuff to haul around), and the voting can be done nearly as fast as the central computer can read in the SD cards. No strange SD cards go into the central machine since they're carried by the same trustworthy human that counts the paper votes.
Yet another issue that paper ballot voting gives us that electronic voting can hardly support is "deniability" of votes: after the fact, you cannot claim to have voted for anyone in particular, so you cannot be bribed or coerced to vote for a given party. This is a very essential and often overlooked property of any voting system.
What things will go wrong? Zillions, I'm sure. But what zillions? I'm curious! A modern processor can't run without it's own software layer. If you want to transfer the data - even if only from an SD card to a local hard drive - then you'd need about seven layers, from which many have sublayers. The lowest level, which is the hardware level, consists on another plethora of levels. If just one transistor is modified by an attacker - or the layout of the transistors or a part of the CPU or a part of the hdd-controller or a part of the SD card controller or... many other things. Then this could lead to the attacker modifying the result of the vote. There are thousands of attack points that start before the voting machine reaches it's target. Then there are attacking vectors that target the SD-card even before there's any voting data on it. (There are SD-card viruses that survive formatting and those aren't even on a hardware level) If you want a decently safe voting machine that costs less than a billion $ to make, then you should use a purely mechanical design. --162.158.90.90 10:22, 13 August 2018 (UTC)
You could all reference Brazil for how an electronic voting system works. It changed in the late 90s after a major country-wide voting fraud scandal that revealed that most of the vote counters in the whole country were unreliable, partisan, bribed or all three; to the point any recount would bring a vastly different result. The Brazilian public lost all faith in the paper ballots and the Federal Electoral Tribunal had to implement an electronic voting system to reacquire voter trust in the voting system.
Twenty years later the public in general still trust the system more than the paper ballot but the losing side in presidential elections always cry afoul about the machines being tampered with (Even though the political parties that complained about fraud for losing the presidential election ended up winning the majority of the seats in both congress and senate, as well as state governships. But, you see, for those elections the system is foolproof, even though they're all done at the same time in the same voting machines.)
- Please sign your comments. The issue is a reduction of points of failure. In a paper ballot system, you have tens of thousands of humans being observed by each other and representatives of interested parties and judges doing the counting. A single malicious person would have to go to incredible effort to hide their miscountings, and then would only be able to change a hundred votes or so. In an electronic voting system, all it takes is one person to do an SD card swap and boom: tens of thousands of votes are changed. One person can change the code on the central counting system that reads the SD cards, and boom: millions of votes are changed. The fact that so much effort would be needed to change the result in a paper ballot system is a security feature. 162.158.62.231 12:00, 11 August 2018 (UTC)
- And anyway, you're describing more or less what already happens in an election. 172.68.58.11 13:54, 11 August 2018 (UTC)
When paper votes need to be re-counted, it's easy: a vote is valid if there is a croos marking at exactly one candidate row. It's possible to implement this in software: store each "paper" as a separate file, and sing it with the voter's private key! Oh, wait, on real paper you don't add your signature because the vote is meant to be anonymous? Tough luck, as long as electronic votes are secret votes, there will be no way to make them re-countable reliably. 141.101.76.82 (talk) (please sign your comments with ~~~~)